What Is SIEM Tools?
SIEM tools stands for Security Information & Event Management. It is a combination of two tools Security Information Management (SIM) & Security Event Management (SEM). SIM is the collection, monitoring, and analysis of security-related data from computer generated logs. While SEM is the practice of network event management including real-time threat analysis, visualization, and incident response. SIEM is a software solution that normalizes, aggregates and analyses activity from various resources across your entire IT infrastructure.
In Short, SIEM is a solution that provides a real time analysis of security alerts generated by computer and network security devices such as Firewall, Router, IDS/IPS, Server, Switch etc.
How Does SIEM Works?

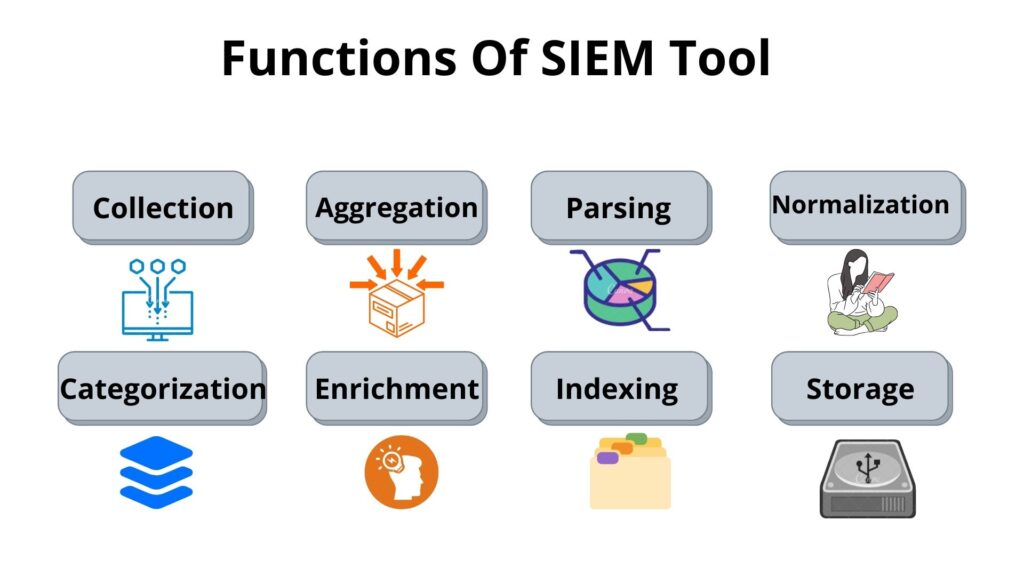
Aggregation: It is a process of collecting security logs from multiple network security devices parsing them, extracting structured data and putting them together in a format (CEF- Common Event Format) that is easily searchable by data tools.
Parsing: Parsing is a software component that can take a specific log format and convert it ti structured data.
Windows logs have different format.
Linux logs have different format.
IDS/IPS have different log format.
Example
Log from xyz firewall
Sep 28 11:45:54 app_server sshd[8677]: failed password for invalid user cybermeteoroid from 150.72.109.227 port 57238
After Parsing
host: app_server
process: sshd
source_user: cybermeteoroid
source_ip: 150.72.109.227
port: 57238
Normalization: Convert structured data into more relevant data which more understandable for human and machine.
host: app_server
process: sshd
source_user: cybermeteoroid
source_ip: 150.72.109.227
port: 57238
After Normalization
Authentication failed | Login | SSh Login | Wrong password
Log Enrichment: log enrichment involves adding important information that can make the data more useful. In this we are trying to give more meaning to the logs.
host: app_server
process: sshd
source_user: cybermeteoroid {administrator}
source_ip: 150.72.109.227 {External IP, Reputation Neutral}
port: 57238
Correlation: In correlation we write a rule or logical expression for alerts and usecases. Like we get 10 failed login attempts from within 1 minutes in our app server, then alert is triggered in console.
Indexing & Storage: Indexing creates an index of common attributes across all logs data, so that search become more efficient and fast. Storage is basically store logs for long term use.
Why SIEM Tools Is Important?
Now, SIEM has become a primary security component of modern organizations. The main reason of using SIEM is to monitor the user activity and any suspicious activity in the network environment. All the activity is done in network generates a log. SIEM systems are designed to use this log data in order to generate insight into past attacks and events.
A SIEM system has the ability to distinguish between legitimate use and a malicious attack. This helps to increase a system’s incident protection and avoid damage to systems and virtual property of an organization.
Future of SIEM And Next Gen SIEM
SIEM is an evolving technology and the next generation of SIEM tools provide new capabilities:
- User and entity behavior analytics (UEBA) in advanced SIEMs go beyond rules and correlations, leveraging AI and deep learning techniques to look at patterns of human behavior. This can help detect insider threats, targeted attacks, and fraud. In UEBA, you do not track security events or monitor devices; instead, you track all the users and entities in your system.
- Security orchestration and automation response (SOAR) is the Next-gen SIEMs integrate with enterprise systems and automate incident response. For example, the SIEM may detect an alert for phishing mail and perform containment steps automatically on affected systems, before the attacker can encrypt the data.
Benefits of SIEM Tools
SIEM tool makes it easier for organizations to manage security by filtering massive amounts of security data/logs and prioritizing the security alerts the software generates.
A SIEM tool can also help an enterprises meet compliance requirements by automatically generating reports that include all the logged security events among these sources. Without SIEM tool, the organization would have to gather log data and compile the reports manually.
The use of SIEM also helps companies to comply with a variety of industry cyber management regulations.
SIEM provides threat detection and security alerts and can perform detailed forensic analysis in the event of major security breaches.
SIEM tool can be used by organizations for a variety of use cases that revolve around data or logs, including security programs, audit and compliance reporting and network troubleshooting.
Limitations of SIEM
SIEM Tool takes long time to implement because it requires support to ensure successful integration with an organization’s security controls and many hosts in its infrastructure.
Analyzing, configuring and integrating reports require the highly skilled people. That’s why some SIEM systems are managed directly within a security operations center (SOC Team), a centralized unit by an information security team that deals with an organization’s security issues.
SIEM tools work on rule to analyze the recorded data. An organization’s network generates a large number of alerts — usually, 10k to 20k per day – which may or may not be positive. Consequently, it’s difficult to identify potential attacks because of the number of these alerts.
Popular SIEM Tools
IBM Qradar
IBM-QRadar SIEM (Security Information and Event Management) is a modular architecture that provides real-time visibility of your IT infrastructure, which you can use for threat detection and prioritization. IBM QRadar collects, processes, aggregates, and stores network data in real time. QRadar uses that data to manage network security by providing real-time information and monitoring, alerts and offenses, and responses to network threats.
Splunk
Splunk is a technology that is used for searching, monitoring, visualizing, and analyzing machine data on a real-time basis. It is a tool for log management and analysis. Splunk is mainly for log management and stores the real-time data as events in the form of indexers. It helps to visualize data in the form of dashboards.
SolarWinds Security Event Manager
SolarWinds Security Event Manager (formerly Log & Event Manager), is a security information and event management (SIEM) virtual appliance that adds value to existing security products and increases efficiencies in administering, managing, and monitoring security policies and safeguards on your network.
Sumologic CSE
Cloud SIEM Enterprise (CSE) is a cloud-based SIEM that provides the collection of log and event data from your infrastructure and applications, on-premise and in-cloud. Correlation of the collected data to winnow down the volume of info you need to sift through to investigate issues. A rich interface that analysts and admins can use to investigate security issues and administer CSE itself.
Arcsight
ArcSight Enterprise Security Manager (ESM), a powerful SIEM that delivers real-time threat detection and native SOAR to your SOC. It reduces threat exposure by detecting threats in real time with powerful and adaptable SIEM correlation analytics.
FAQ
1 What is an Information Security?
Information Security sometimes called InfoSec, act of protecting data & information from unauthorized access, unlawful modification & disruption, disclosure & destruction. Read more
2 What is AAA in cybersecurity?
AAA (Authentication, Authorization, Accounting) is a system for tracking user activities on IP based network & controlling their access to network. Read more
3 What is Malware?
Malware is malicious software or program designed to infiltrate a computer system/network and possible damage it without the user’s knowledge or consent. Read more
4 What is Cyber Kill Chain?
The cyber kill chain (also referred to as the cyber-attack chain ) is a way to understand the sequence of events involved in an external attack on an organization’s IT environment Read more
5 What is Public Key Cryptography?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. Read more
6 Difference between Stream & Block Cipher?
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Read more

