The Advanced Encryption Standard (AES) algorithm is a symmetric-key block cipher (block size 128 bit) encryption designed & by published by the National Institute of Standards and Technology (NIST) in 2001. AES algorithm is widely used today as it is a much stronger than DES and 3DES. In Advanced Encryption Standard number of rounds depends on the key length, 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys.
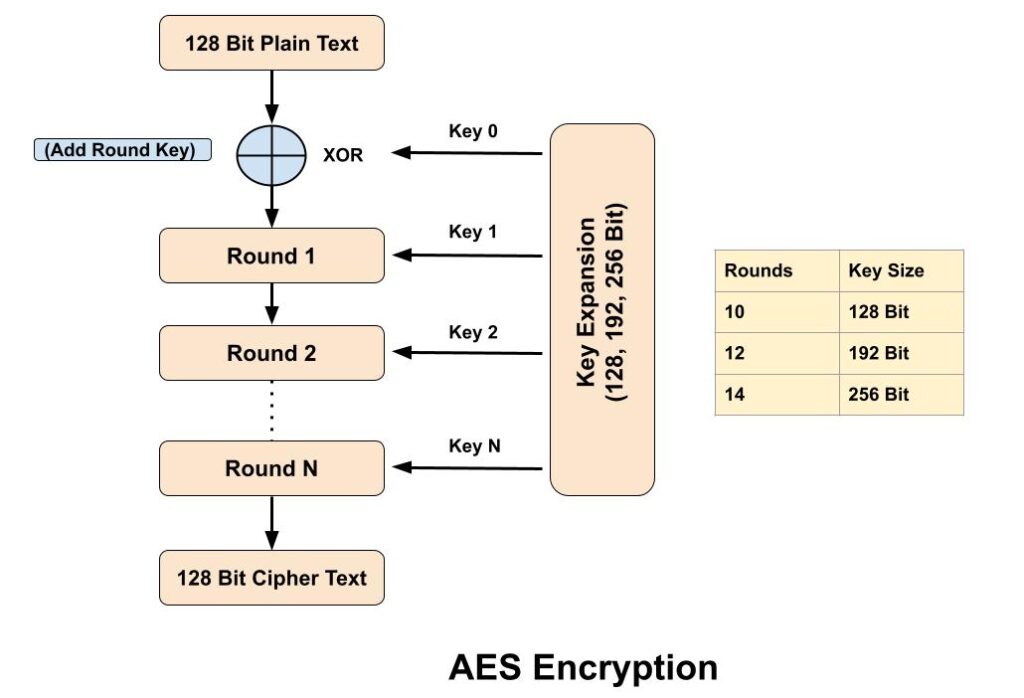
Advanced Encryption Standard takes 128 bits plain text as input and produced 128 bits cipher text as output. It’s encryption process is based on a substitution-permutation network, also referred as an SP network. It consists of a series of linked operations, including replacing inputs with specific outputs (substitutions) and others involving bit shuffling (permutations). AES algorithm also known as the Rijndael Algorithm.
The main features of AES algorithm are as follows–
1. AES algorithm is symmetric key symmetric block cipher.
2. AES encryption speed is faster than RSA Encryption.
3. AES uses only single key for both encryption and decryption.
4. Number of rounds depends on key length 128 bits – 10 Round 192 bits – 12 Round 256 bits – 14 Round.
How does AES algorithm work?
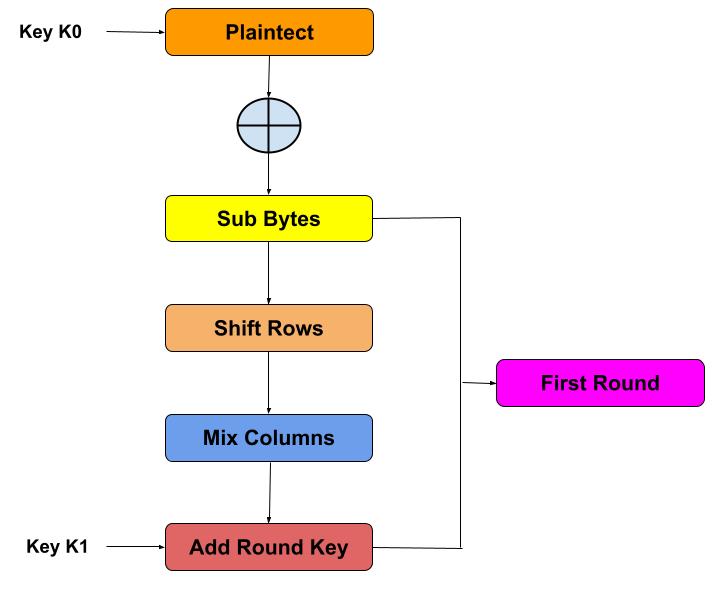
AES encryption process is based on a substitution-permutation network. AES encryption treats the 128 bits of a plaintext block as 16 bytes. Suppose we want to encrypt this text “I LOVE BATMAN” then we know that AES is a block cipher so it breakdown this text into a block (4*4 state array). And we are assuming the Key K0 is “DRAGONBALLZSUPER”.

Add Round Key: In this step XOR operation is performed between data stored in the state array and key K0. And pass the resultant state array on as input to the next step.

Sub-Bytes: In this step, it converts each byte of the state array into hexadecimal. AES algorithm substitutes every byte with a code according to a pre-established table called the S-box. After the process of byte substitution, block of cipher might take the appearance of something look like this (keep in mind that it’s still a hypothetical representation of what the real deal looks like):

Shift Rows: In this step, all rows are shifted except the first row, the second row gets shifted to the left by one byte, the third row moves to the left by two bytes, while the forth one gets shifted by three bytes.

Mix Columns: In this step, a pre-defined matrix multiplied with each column of above resultant array to get a new column for the subsequent state array. We are assuming the new column look like this as shown in below.

Add Round Key: In this step, XOR operation is performed between state array is obtained in the previous step with the Key K1.And the resultant of this step goes to the round 2 as the input array.

Real use case of AES algorithm
- Wi-Fi: Wireless networks like WPA2 use AES encryption.
- Compression Tools: File compression tools like WinZip and RAR are also use AES algorithm.
- Microprocessor Security: Microprocessor manufacturers enable hardware-level encryption using the likes of AES encryption to bolster security.
Related Questions & Answers
1 What is cryptography?
Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information, so that only those for whom the information is intended can read and process it. In information Read more
2 What is DES Algorithm?
Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption designed by an IBM team and published by the National Institute of Standards and Technology (NIST).
It uses the same key to…Read more
3 What is Private Key Cryptography?
Symmetric cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message… Read more
4 Difference between DES & AES algorithm?
Data Encryption Standard (DES) and Advanced Encryption Standard (AES) algorithm, both are the symmetric block cipher. DES structure is based on feistal network while AES structure is based S-P network. Read more
5 What is Public Key Cryptography?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. he private key should not be… Read more
6 Difference between Stream & Block Cipher?
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Both Stream Cipher and Block Cipher are…Read more

