What is DES Algorithm?
The Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption designed by an IBM team and published by the National Institute of Standards and Technology (NIST). It is symmetric key cryptography, so it uses the same key to encrypt and decrypt a message and key length is 56 bits. DES is a block cipher and encrypts data in blocks size of 64 bits each, which means 64 bits of plaintext goes as the input to DES, and produces 64 bits of cipher text. The DES algorithm encryption process breaks down into the following steps:
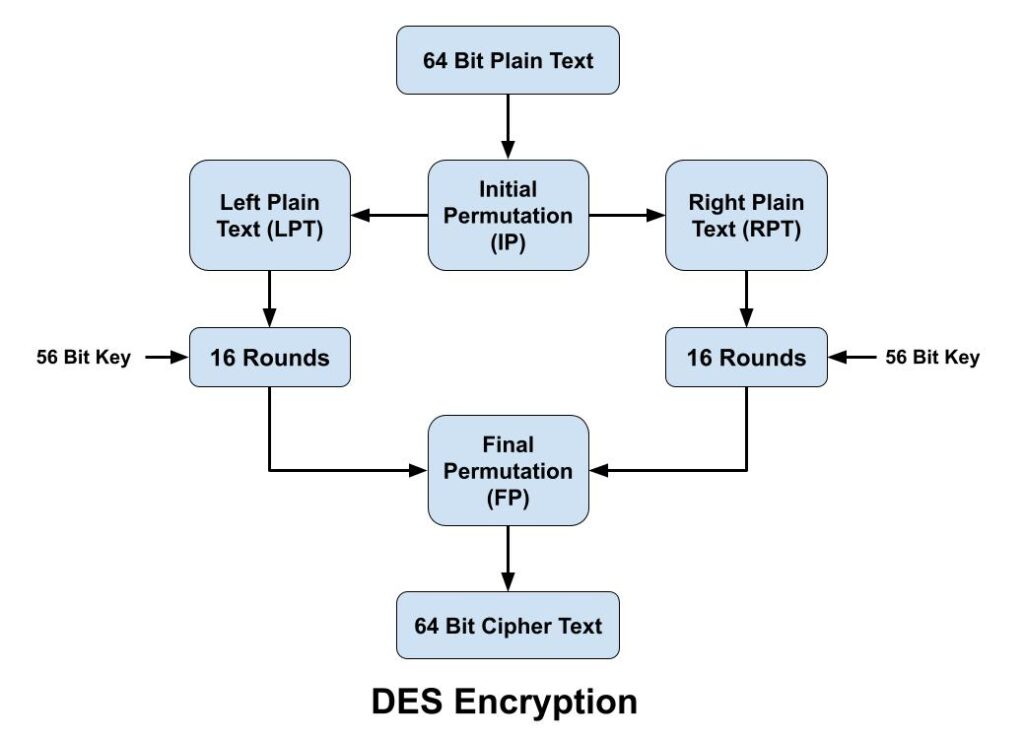
1. In first step, the 64-bit plain text block is handed over to an initial Permutation (IP) function.
2. Initial permutation (IP) is then performed on the given plain text.
3. The IP produces two halves of the permuted block, known as Left Plain Text (LPT) and Right Plain Text (RPT).
4. Both LPT and RPT go through 16 rounds of the encryption process.
5. Finally, both LPT and RPT are recombined, and a Final Permutation (FP) is performed on the newly combined block.
6. Finally 64-bit cipher text is produced.
The encryption process step (step 4, above) is further broken down into five stages:
Key transformation
Expansion permutation
S-Box permutation
P-Box permutation
XOR and swap
Key Transformation: Initial 64-bit key is transformed into a 56-bit key by discarding every 8th bit of the initial key. From this 56-bit key, a different 48 bit Sub Key is generated during each round using a process called key transformation. In short the key transformation process compresses the 56-bit key to 48 bits.
Expansion permutation: After initial permutation, two 32-bit plain text areas called Left Plain Text (LPT) and Right Plain Text (RPT) are produced. During the expansion permutation, a half-block of 32-bits is expanded to 48 bits. It adds adjacent bits from each side of the block to the 32-bits of the block to create a 48-bit block.
S-Box permutation: A substitution box permutation (S-box) is the only non-linear component in the DES algorithm. It gives additional security to the cipher block. After the block is mixed with the sub-key, it is divided into eight 6-bit parts. The S-box process uses a lookup table to convert this eight 6-bit parts into 4-bit output each, resulting in 32-bit output in total.
P-Box permutation: The 32-bit output from the S-box permutation is reposition according to the P-box permutation.
XOR and Swap: XOR is a mathematical function that compares two sets of bits that can be either 1s or 0s. If the bits from both sets match, the XOR output is 0. On the other hand, if they don’t match, the output is 1. This bit-wise comparison results in stronger encryption.
The method of decryption uses the same algorithm, but it is done in reverse order of the same key as the DES algorithm is the symmetric key algorithm.
Advantages of DES Algorithm
DES algorithm is easy to implement because of its Feistel structure and basic or uncomplicated logic.
Data Encryption Standard (DES) algorithm works fast in hardware.
Both encryption & decryption uses same keys.
Disadvantages of DES Algorithm
DES was mainly designed for hardware so it runs relatively slow on software compared to hardware.
DES can be broken easily as it has known vulnerabilities. And due to smaller key, which make it less secure.
DES is vulnerable to a differential, and Brute Force attacker could be analyzed plaint text using differential cryptanalysis.
Triple DES (3DES) Algorithm
The Triple Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption. It uses the Data Encryption Standard (DES) cipher three times to encrypt its data that why it is referred as 3DES. 3DES operates in three basic steps: Encrypt-Decrypt-Encrypt (EDE). It works by taking three 56-bit keys (K1, K2 and K3), encrypting with the first key (k1), decrypting with the second key (k2), and encrypting with the third key (k3). A two-key variant also exists, where k1 and k3 are the same. Note that if K1 = K2 = K3, then Triple DES is really Single DES.
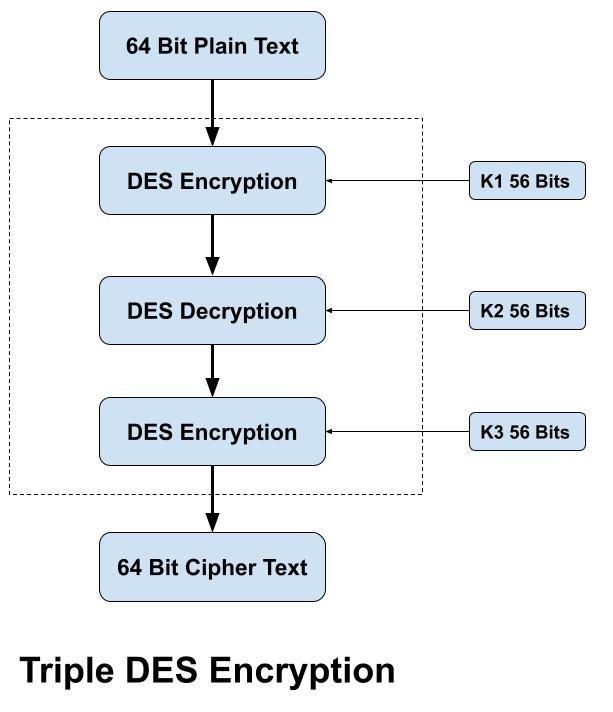
The 3DES algorithm process breaks down into the following steps:
Encrypt the plaintext using the DES algorithm with first key (K1).
Decrypt the resulting encrypted output using the DES algorithm with second key (K2).
Encrypt the resulting decrypted output using the DES algorithm with third key (K3).
Although 3DES is more secure than DES, but it still remains vulnerable to certain kinds of attacks like meet-in-the middle attack and block collision attack.
Difference between DES and 3DES
| Factor | DES Algorithm | 3DES Algorithm |
| Key Length | DES has 56 Bits key length | 3DES has 128 Bits key length |
| Cipher | DES is a block cipher | 3DES is also a block cipher |
| Block Size | It has 64 Bits block size | 3DES also has 64 Bits block size |
| Speed | Encryption/Decryption speed is slow but fast as compared to 3DES | It’s encryption/decryption speed is the lowest among all algorithm. |
| Security | DES is less secure. | 3DES is a three times more secure as compared to DES |
| No of Rounds | DES has 16 rounds | While 3DES has 48 rounds |
Conclusion
All DES, 3DES are used for encryption of the data and are useful in their own way. 3DES came as the successor of DES to overcome its drawbacks. DES is the older algorithm and 3DES is the advanced algorithm which is more secure compared to DES. Although DES had made great contributions in the field of data security, but now it is replaced by 3DES in the areas of high security.
Related Question & Answer
1 What is cryptography?
Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information, so that only those for whom the information is intended can read and process it. In information Read more
2 What is Private Key Cryptography?
Symmetric cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message… Read more
3 What is Public Key Cryptography?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. he private key should not be… Read more
4 Difference between Stream & Block Cipher?
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Both Stream Cipher and Block Cipher are…Read more

