Cyber Kill Chain
The cyber kill chain (also referred to as the cyber-attack chain ) is a way to understand the sequence of events involved in an external attack on an organization’s IT environment. Understanding the cyber-attack chain model can help IT security teams put strategies and technologies in place to “kill” or contain the attack at various stages, and better protect the IT ecosystem.
The cyber kill chain model was developed by Lockheed Martin to break down the structure of a cyber-attack (either offensive or defensive) into a pattern composed of identifiable stages.
Lockheed Martin’s cyber kill chain breaks down an external attack into 7 distinct steps:
- Reconnaissance: The attacker determines what methods to use to complete the phases of the attack. Attacker picks a target, researches it, and looks for vulnerabilities.
- Weaponization: The attacker couples payload code that will enable access with exploit code that will use a vulnerability to execute on the target system. Or Intruder develops malware designed to exploit the vulnerability.
- Delivery: The attacker identifies a vector by which to transmit the weaponized code to the target environment. The vector may be a phishing email or another medium.
- Exploitation: The weaponized code is executed on the target system by this mechanism.
- Installation: This mechanism enables the weaponized code to run a remote access tool and achieve persistence on the target system. Or in short weaponized code installs a backdoor or other ingress accessible to the attacker.
- Command & Control (C2): The weaponized code establishes an outbound channel to a remote server that can then be used to control the remote access tool and possibly download additional tools to progress the attack.
- Actions on Objectives: The attacker typically uses the access he has achieved to covertly collect information from target systems and transfer it to a remote system (data exfiltration) or achieve other goals and motives.
Cyber Kill chain analysis can be used to identify a defensive course-of-action matrix to counter the progress of an attack at each stage. Over the years, the attack landscape has shifted, and many have argued that the cyber kill chain, while helpful, needed to be updated to accommodate the reality that the traditional perimeter has shifted—some even say it has, in many cases, vanished.
Mitre ATT&CK Framework
Mitre ATT&CK framework is knowledge base maintained by the MITRE Corporation for listing and explaining specific adversary tactics, techniques, and common knowledge or procedures used by threat hunters, red teamers, and defenders to better classify attacks and assess an organization’s risk.
Mitre ATT&CK framework consists of total 14 tactics.
| Name | Description |
| Reconnaissance | The adversary is trying to gather information they can use to plan future operations. |
| Resource Development | The adversary is trying to establish resources they can use to support operations. |
| Initial Access | The adversary is trying to get into your network. |
| Execution | The adversary is trying to run malicious code. |
| Persistence | The adversary is trying to maintain their foothold. |
| Privilege Escalation | The adversary is trying to gain higher-level permissions. |
| Defense Evasion | The adversary is trying to avoid being detected. |
| Credential Access | The adversary is trying to steal account names and passwords. |
| Discovery | The adversary is trying to figure out your environment. |
| Lateral Movement | The adversary is trying to move through your environment. |
| Collection | The adversary is trying to gather data of interest to their goal. |
| Command and Control | The adversary is trying to communicate with compromised systems to control them. |
| Exfiltration | The adversary is trying to steal data. |
| Impact | The adversary is trying to manipulate, interrupt, or destroy your systems and data. |
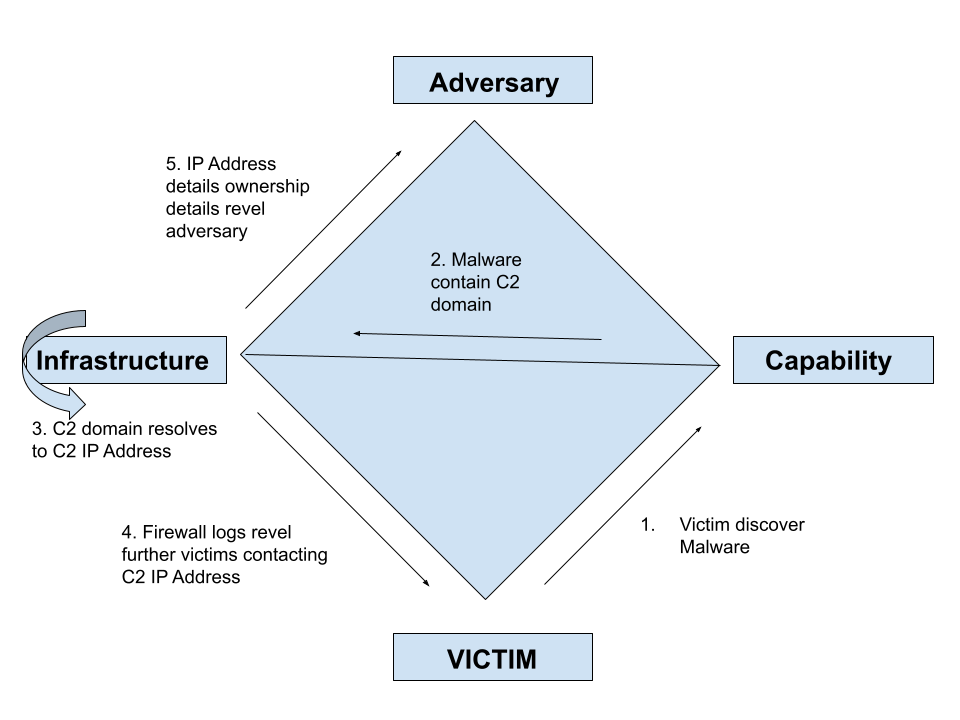
Diamond Model of Intrusion Analysis
Diamond model of intrusion analysis is framework for analyzing cybersecurity incidents and intrusions by exploring the relationships between four core features: adversary, capability, infrastructure, and victim.
Read More
What is cybersecurity & why it is important ?
CIA Triad & AAA in Information Security
What is malware and its different types ?


Awsome site! I am loving it!! Will be back later to read some more. I am bookmarking your feeds also.
I have been reading out many of your posts and i must say nice stuff. I will definitely bookmark your blog.