Elliptic curve cryptography (ECC) is a public-key based on the mathematics structure of elliptic curves. ECC implements all major capabilities of the asymmetric cryptosystems like key exchange, signatures and encryption.
ECC cryptography is considered a modern successor of the RSA cryptography. Because ECC has smaller keys size and signatures as compared to RSA algorithm. And provide same level of security, also provides very fast key generation & fast key agreement.

How does it works?
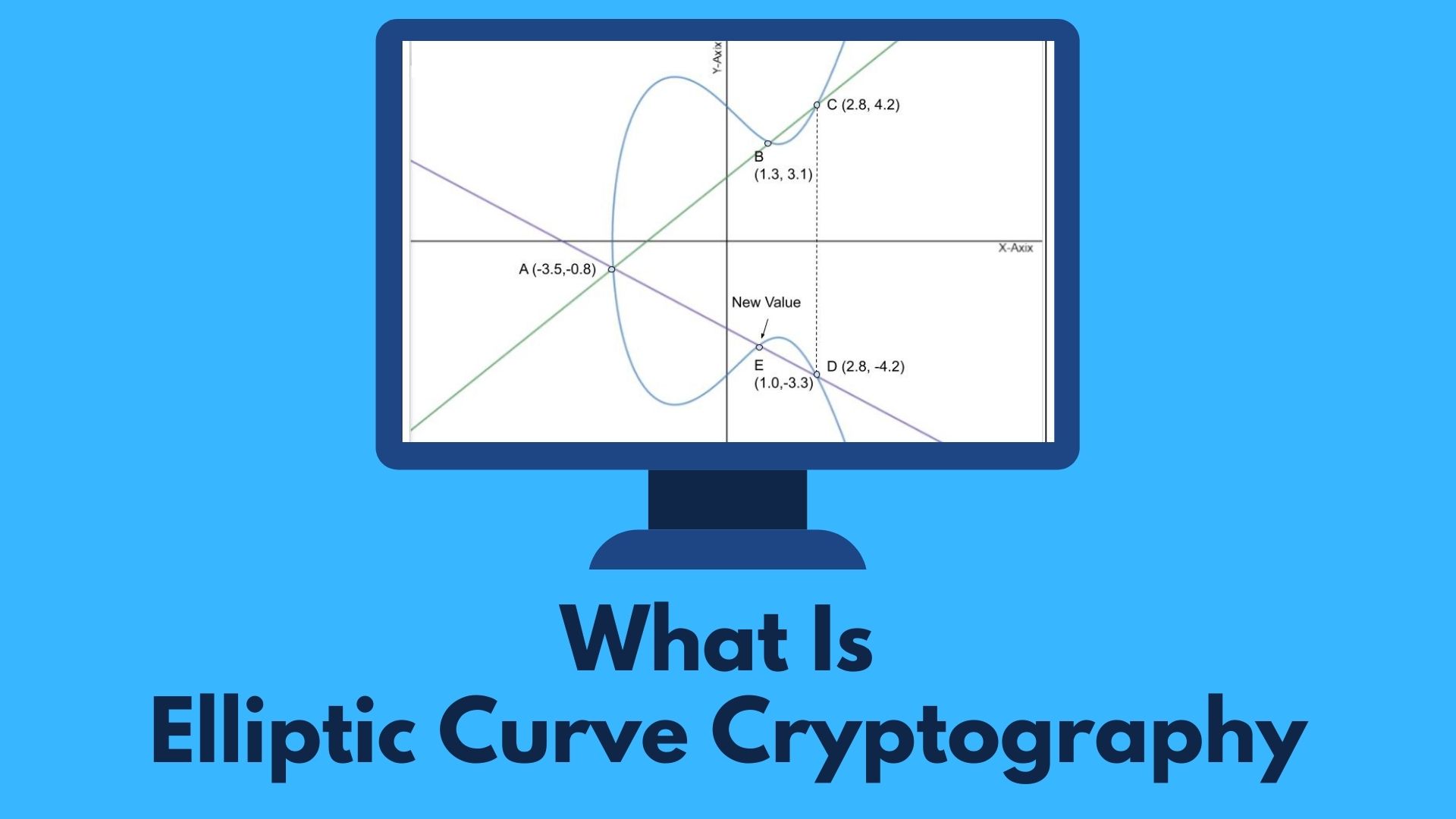
An elliptic curve is the set of points that satisfy a specific mathematical equation. The equation for an elliptic curve looks like this y2=x3+ax+b and is being represented graphically like the image below.

ECC generates public & private keys through the properties of an elliptic curve equation instead of the traditional method of generation as the product of large prime numbers. In RSA cryptography, where both keys are integers, while in ECC the private and public keys are not equally exchangeable. Instead the public key is a point on the curve, while the private key is still an integer.
Multiplying points A & B on the curve by a number produces another point on the curve (C).
Mirror the point (C) on the opposite side of the x-axis produces point D.
From point D, a line is drawn back to our original point A, creating an intersection at point E.
This process can be completed n number of times within a defined max value. Here, n is the private key value, which indicates how many times the equation should be run.
The maximum defined value of the equation depends to the key size used.
Remember, by knowing two points, say, A and B, the other point, C, can be found, but with just C, the other two points, A and B, cannot be calculated.
Elliptic curve cryptography (ECC) vs RSA Algorithm
| ECC Algorithm | RSA Algorithm |
| It stands for Elliptic-curve cryptography. | It Stands for Rivest, Shamir and Adleman. |
| ECC works on the mathematical representation of elliptic curves. | While RSA works on the principle of the prime factorization method. |
| ECC is slower due to complex its nature. | RSA is faster as compared to ECC algorithm. |
| ECC provides same security as RSA and required shorter key length. (ECC 256 bit = RSA 3072 bit) | RSA requires larger length for security. (ECC 256 bit = RSA 3072 bit) |
| Public key is a point on curve and private is an integer in ECC algorithm. | Both public and private key are an integers in RSA algorithm. |
| ECC utilize less CPU and memory resources as compared to others asymmetric key cryptography. | RSA required more CPU and memory resources. |
| ECC features smaller ciphertexts, keys, and signatures. | While RSA has larger key sizes and signatures. |
Applications of Elliptic curve cryptography
Elliptic curve based cryptography are gaining popularity and the pace of adoption is accelerating. It is now used in a variety of applications.
- It is applicable for encryption, digital signatures, pseudo-random generators and other tasks.
- ECC is used in authentication method for secure web browsing over SSL/TLS.
- Apple messaging service “iMessage” used ECC algorithm for signatures.
- Domain name system uses ECC algorithm to encrypt the DNS information with DNSCurve.
- Elliptic curve cryptography to provide perfect forward secrecy which is important for online privacy.
- It is used by the cryptocurrency bitcoin, ethereum to verified a particular transaction.
Advantages of Elliptic Curve Cryptography
Elliptic curve cryptography key size of 256-bit is equal to a 3072-bit RSA key, which is 10,000 times efficient than a 2048-bit RSA key.
Elliptic curve cryptography uses simpler and smaller keys, size is one of the prime advantages of elliptic curve cryptography as compared to other asymmetric cryptography.
Perfect Forward Secrecy (PFS) is also an important benefit of Elliptic curve cryptography.
ECC provide equivalent security with lower computing power and battery resource. So it is widely used for mobile applications and IoT devices with limited central processing unit (CPU) resources.
Major Disadvantages of Elliptic Curve Cryptography
The main disadvantage of ECC algorithm is that it isn’t easy to implement due to its complexity. As Compared to RSA which is much simpler on both side encryption/decryption and authentication.
Key generation in elliptic curve cryptography is slow while in RSA cryptography key generation process is much faster.
Related Questions & Answers

Diffie Hellman algorithm is a method for securely exchanging cryptographic keys.
Read more

AES takes 128 bits plain text as input and produced 128 bits cipher text as output.
Read more

RC4 is a stream cipher, symmetric key encryption algorithm.
Read more

IDEA encrypts a 64-bit block of plaintext to 64-bit block of cipher text.
Read more
RSA algorithm is an asymmetric cryptography uses two different keys –one public & one private.
Read more
Zero-day vulnerability involving remote code execution in Log4j 2 was published by the Alibaba Cloud Security Team.
Read more

Blowfish is a symmetric block cipher, has a 64-bit block size and a variable key length.
Read more
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data.
Read more
Learn More About Cryptography
1 What is cryptography?
Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information, so that only those for whom the information is intended can read and process it. In information Read more
2 What is Private Key Cryptography?
Symmetric cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message… Read more
3 What is Public Key Cryptography?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. he private key should not be… Read more
4 Difference between Stream & Block Cipher?
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Both Stream Cipher and Block Cipher are…Read more