Blowfish algorithm is an encryption technique introduced in 1993 by Bruce Schneier. Blowfish is a symmetric block cipher, meaning that it uses the same secret key to both encrypt and decrypt messages. It can be used as a replacement for DES or IDEA.
Blowfish has a 64-bit block size and a variable key length from 32 bits up to 448 bits. It is a 16-round Feistel cipher. It is significantly faster than DES and provides a good encryption rate. Blowfish is unpatented and license-free, and is available free for all uses.
Main features of Blowfish Algorithm
Speed: Blowfish encryption state on 32 bit microprocessors.
Compact: Blowfish algorithm can execute in less than 5KB memory.
Structure: It uses feistel structure by which you can quickly transform any function into a permutation.
License Free: Blowfish is a license-free, and is available in the public domain.
Round: Blowfish Algorithm runs 16 times i.e. 16 rounds.
How Does Blowfish Algorithm Works?
Blowfish makes use of an SP network, the first step is to initiate the substitution box (S-box) & permutation box (P-box). There are 18 P-arrays with 32-bit subkeys and 4 32-bit S-boxes with 256 entries each.
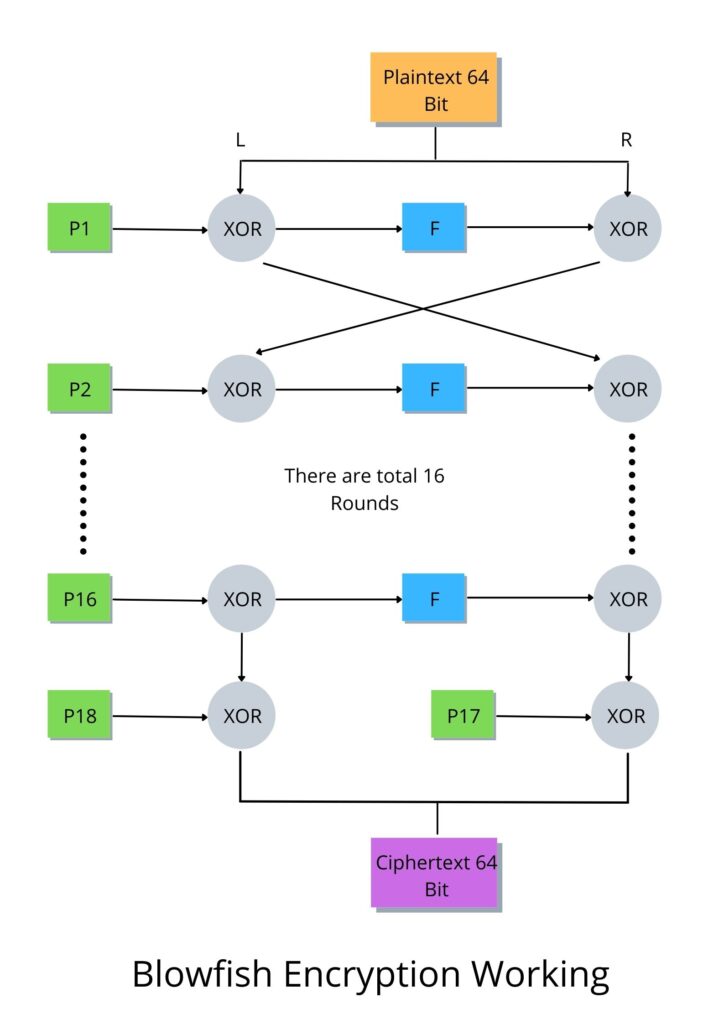
Step 1: In first step, we split 64-bit of plaintext into two equal blocks, L and R 32-bit each.
Step 2: In next step, we enter an encryption cycle that runs 16 times and the following steps take place in each loop:
- The first element in the P-array (P1) is now XORed with the L.
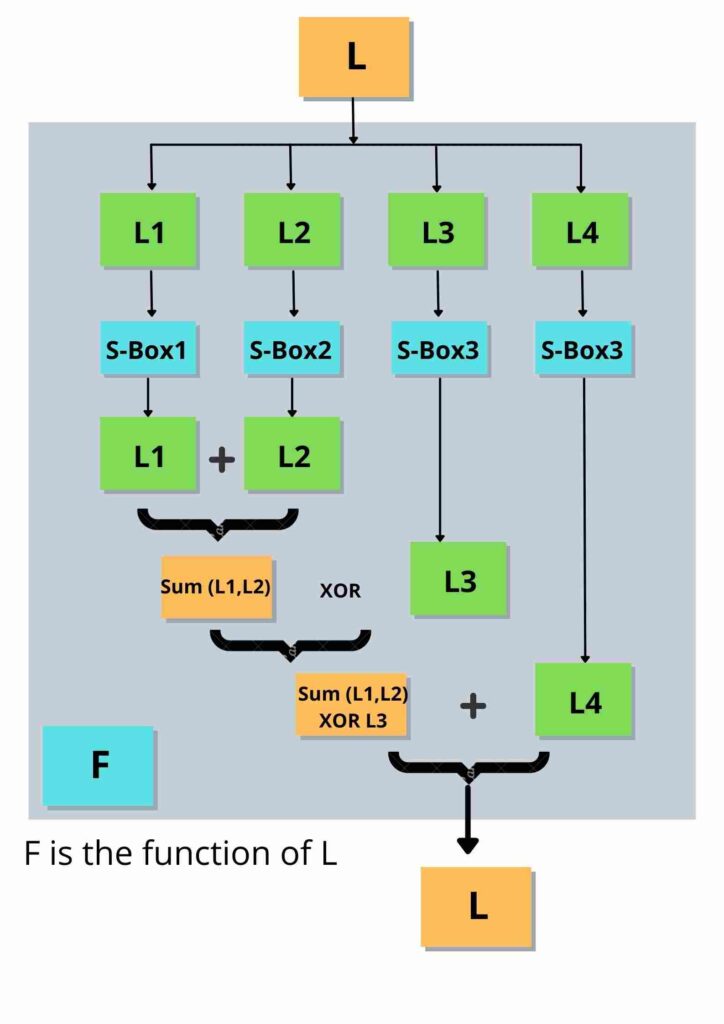
- then XOR R with F, F is a function of L that makes use of the S-box split into 4 blocks. The complete overview of function F is shown below.
- After that, L and R are swapped before the loop enters its next iteration.
Step 4: After the loop finishes, L and R are swapped once more.
Step 5: The last two unused P-box (P17 & P18) entries by XORing R with P17 and L with P18.
Final Step 6: In last step, we combine L and R to retrieve the cipher text.
Major Drawback of Blowfish Algorithm
Blowfish is significantly faster than DES and IDEA. However, it couldn’t completely replace DES due to its small block size, which is considered insecure. The creator of Blowfish, Bruce Schneier, improved on this flaw by coming up with the Twofish encryption algorithm, which had a block size of 128 bits. Blowfish algorithm has never been broken, and the algorithm is included in many cipher suites and encryption products available today.
What is Twofish Algorithm?
Twofish is the successor to Blowfish, it is a symmetric-key block cipher with a block size of 128 bits and variable-length key of size 128, 192 or 256 bits. This technique is one of the fastest encryption algorithms and is ideal for both hardware and software environments.
It was a selected for the National Institute of Technology and Science (NIST) to find a replacement for the Data Encryption Standard (DES) encryption algorithm but in the end it was not selected for standardization. It is completely free, and there are no patent royalties on the algorithm, copyright on the code, or any license fees.
Advantages of Blowfish
- Blowfish algorithm is faster than other encryption algorithms, such as the Data Encryption Standard (DES) and IDEA encryption.
- It is unpatented and license free, means anyone can take and use Blowfish for whatever they want to, without paying the creator.
- Blowfish encryption is more efficient because it has a lesser amount of operations to complete compared to other encryptions.
Disadvantages of Blowfish
- Blowfish has a smaller block size, so it is vulnerable to Birthday Attacks and compromise the encryption algorithm.
- The key schedule of Blowfish takes a long time.
Applications of Blowfish Algorithm
Password management: Password management tools like Java PasswordSafe and Access Manager use blowfish to create passwords and encrypt saved passwords.
Backup Tools: Backup software like Symantec NetBackup also uses blowfish algorithm to encrypt information in the backup.
Disk Encryption: File/Disk encryption tools such as Bcrypt and CryptoForge use blowfish encryption to keep sensitive data secure.
Remote Access Tools: Software like OpenSSH and PuTTy use blowfish to securely remote access of a computer in a network.
Many social media platforms and e-commerce websites also use Blowfish encryption to protect user data.
Related Questions & Answers

Diffie Hellman algorithm is a method for securely exchanging cryptographic keys.
Read more

AES takes 128 bits plain text as input and produced 128 bits cipher text as output.
Read more

RC4 is a stream cipher, symmetric key encryption algorithm.
Read more

IDEA encrypts a 64-bit block of plaintext to 64-bit block of cipher text.
Read more
RSA algorithm is an asymmetric cryptography uses two different keys –one public & one private.
Read more
Zero-day vulnerability involving remote code execution in Log4j 2 was published by the Alibaba Cloud Security Team.
Read more
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data.
Read more
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data.
Read more

