Diffie Hellman key exchange algorithm is a method for securely exchanging cryptographic keys over a public communications channel. The Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure channel.
Keys are not actually exchanged – they are jointly derived. Diffie Hellman key exchange algorithm can be used for only key exchange, not for encryption and decryption process.
DH is generally explained by two sample parties, Aman (Sender) and Tarun (Receiver), initiating a dialogue. Both party generates a public/private key pair and distributes the public key.
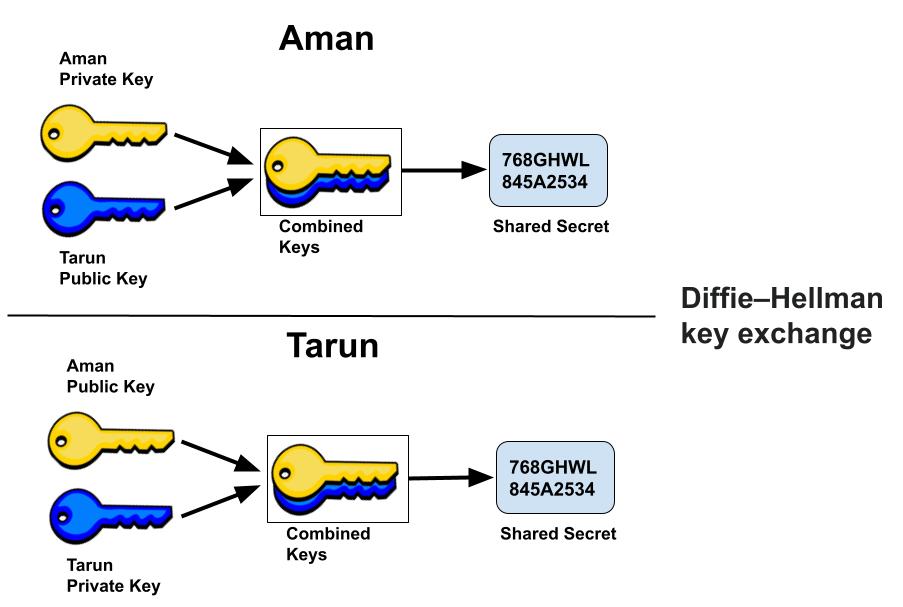
After obtaining an authentic copy of each other’s public keys, Aman and Tarun can compute a shared secret offline. The shared secret can be used, for instance, as the key for a symmetric cipher. Since it doesn’t authenticate any party in the transmission, so the Diffie Hellman key exchange is susceptible to a man-in-the-middle attack.
Where is the Diffie-Hellman key exchange used?
Diffie-Hellman key exchange is implemented in security protocols such as Transport layer Security (TLS), IPsec, Pretty Good Privacy (PGP), and many others. This makes it an integral part of our secure communications.
ElGamal algorithm, which was used heavily in PGP, is based on the Diffie-Hellman key exchange.
Secure Shell (SSH): SSH is a cryptographic protocol used to access system terminals from a third-party appliance or application. The Diffie-Hellman algorithm assists in exchanging the keys between both systems before enabling remote access.
Advantages of the Diffie Hellman key exchange
- The sender and receiver don’t need any prior knowledge of each other.
- Once the keys are exchanged, the communication of data can be done through an insecure channel.
Disadvantages of the Diffie Hellman key exchange
Diffie Hellman Algorithm cannot be used for signing digital signatures.It should be used in conjunction with a recognized authentication method such as digital signatures algorithm.
It doesn’t authenticate any party in the transmission, so Diffie Hellman key exchange is vulnerable to a man-in-the-middle attack.
Diffie-Hellman key exchange algorithm with RSA algorithm
We know that it does not provide any authenticate for the connection that why Diffie-Hellman key exchange is often implemented alongside RSA or other algorithms to provide authentication for the connection.
RSA allows its users to encrypt the information with their correspondent’s public key, so that they can only be decrypted by the matching private key. But in practice, RSA isn’t used to encrypt the whole of the communications–this would be inefficient.
Alternatively, the Diffie-Hellman key exchange can be combined with other algorithms like the Digital Signature Standard (DSS) to provide authentication, key exchange, confidentiality and check the integrity of the information.
Related Questions & Answers

RC4 is a stream cipher, symmetric key encryption algorithm.
Read more

IDEA encrypts a 64-bit block of plaintext to 64-bit block of cipher text.
Read more
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data.
Read more
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data.
Read more
Symmetric
cryptography popular as private key cryptography, uses a single key to encrypt data.
Read more

Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information,
Read more
RSA algorithm is an asymmetric cryptography uses two different keys –one public & one private.
Read more
Zero-day vulnerability involving remote code execution in Log4j 2 was published by the Alibaba Cloud Security Team.
Read more

