What is Virtualization ?
Virtualization is the act of creating a virtual version of something (rather than actual version) like Operating system, storages devices. Virtualization deploys software that makes an abstraction layer across computer hardware, letting the hardware components such as processors, memory, storage etc of a particular computer to be segmented into several virtual elements (also known as virtual machines). A virtual machine is a container for an emulated computer that runs an entire operating system.
Virtualization technology allows corporates to apply a cloud based delivery model to their on-site infrastructure to improve internal security, workflows and performance. Corporates can also virtualize their infrastructure, software or platforms to deliver a range of services to their end-users.
Types of Virtual Machines
- System Virtual Machine: These types of VMs provide full virtualization. Complete platform designed to replace an entire physical computer and includes a full desktop/server operating system. Hardware resources are shared and managed, forming multiple environments on the host system. These environments are isolated from each other but exist on the same physical host.
- Processor Virtual Machine: These VMs are also known as Application virtual machines, Managed runtime environments. These VMs are designed to only run a single process or application like a virtualized web browser or a simple web server. It is created with the starting of the process and is destroyed when the process ends.
What Is Hypervisor & Its Types ?
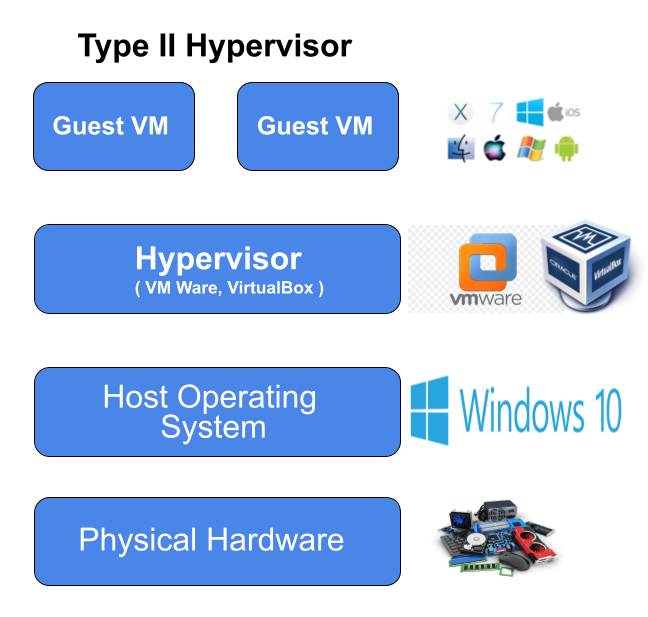
Hypervisor manages the distribution of the physical resources of a host machine (server) to the virtual machines being run (guests). In other words virtualization software uses a thin layer of software, known as a hypervisor, which allows one computer to host multiple virtual machines (VMs). VMs are software containers that run their own operating systems and behave like independent computers–despite running on a small share of the underlying hardware. Hypervisors are basically two types Type I and Type II. Type I known as bare metal hypervisor, are more efficient as compared to Type II hypervisors.

What is Containerization ?
Containerization is similar to virtualization but it removes guest OS & runs application directly through docker or container engine. In Containerization a single operating system kernel is shared across multiple virtual machines but each virtual machine receives its own user space( known as container) for programs and data. Containerization allows for rapid and efficient deployment of distributed applications.
In Containerization, Each container is an executable package of software, running on top of a host OS. A host(s) may support many containers (tens, hundreds or even thousands) concurrently, such as in the case of a complex microservices architecture that uses numerous containerized ADCs. This setup works because all containers run minimal, resource-isolated processes that others cannot access.

Virtualization vs Containerization
| Parameters | Virtualization | Containerization |
| Guest OS | Each VM runs its own OS (Guest OS) | All containers share the same kernal of the host |
| Startup Time | VMs take s few minutes to bootup | Containers can be booted up in a few seconds |
| Storage | VM take more storage as the whole OS kernal have to be installed | Container take less storage as its host OS is shared |
| Quantity | Cannot run more than a couple of VMs on an average desktop | Can run many of container in a desktop. |
| Security | Vms are fully isolated and hence more secure | Containers have process level isolation & less secure |
| Cost | VMs have lower cost but higer compared to containers | Containers have extremely low cost due to single host |
| Providers | VM Ware, VirtualBox and Hyper-V | Docker, OpenVZ and Parallels Virtuozzo |
Threats to VMs
- VM Escape: An attack that allows an attacker to break out of a normally isolated VM by interacting directly with the hypervisor. Due to this attacker can access from single VM to others VM.
- Data Remnants: Contents of a virtual machine that exist as deleted files on a cloud-based server after deprovisioning of a virtual machine.
- Privilege Elevation: Occurs when a user is able to grant themselves the ability to run functions as a higher-level user.
- Virtualization Sprawl: Occurs when virtual machines are created, used, and deployed without proper management or oversight by the system admins. In virtualization Sprawl administrator can no longer effectively control & manage all the VM on a Network.
Always Delete the unnecessary VMs that are no longer needed.
Read More About Security
What is Botnet, Backdoor, Logicbomb ?
What is cybersecurity & why it is important ?
CIA Triad & AAA in Information Security
What is malware and its different types ?
Threat Hunting: Hunting Techniques & Methodologies


4 thoughts on “Virtualization & Hypervisor In Cloud Computing”