What Is Denial Of Service (DoS) Attack?
A DOS attack is a denial of service attack, in this attack a hacker sends huge amount of traffic to a victim’s computer and shuts it down. Denial of Service (DoS) attack is an online attack which is used to make the website server resources unavailable for its users. Basically In this attack, victim’s computer/server is bombarded with traffic from the hacker’s system and shut down its services.
What Is Distributed Denial Of Service (DDoS) Attack?
A DDoS attack is a distributed denial-of-service attack where a group of compromised systems attack simultaneously a single target to create a Denial of Service (DOS).In DDoS attack victim’s computer is bombarded with traffic from multiple systems across different locations so that victim’s computer resources make unavailable. If this attack happened in networks, the server becomes inaccessible to all its users.
Types of DoS and DDoS Attacks
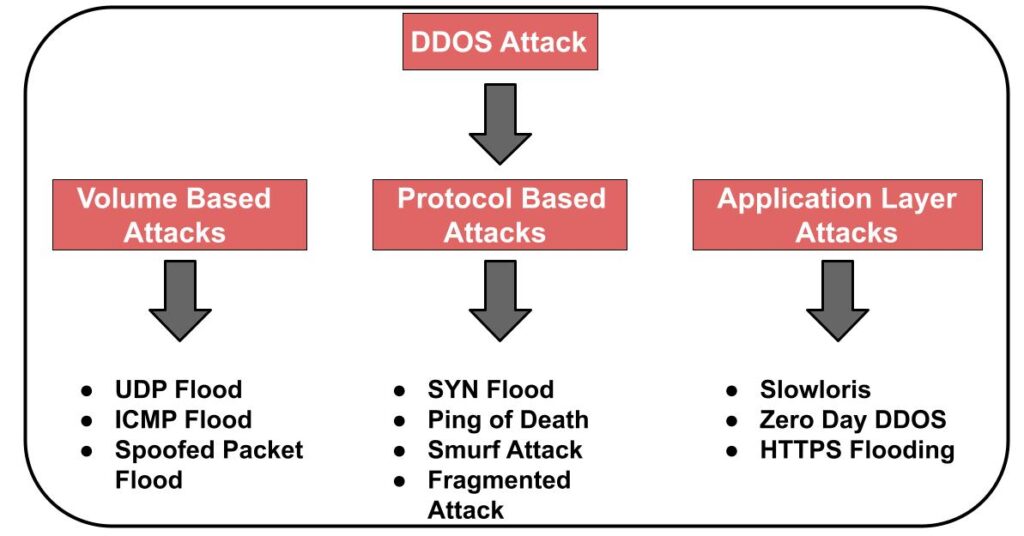
1. UDP Flood Attack
In this attack a large number of User Datagram Protocol (UDP) packets are sent to a targeted server with the aim of overwhelming that device’s ability to process and respond. When a server receives a UDP packet at a particular port, then it goes through two steps in response:
- The server first checks to see if any programs are running which are presently listening for requests at the specified port.
- If no programs are receiving packets at that port, the server responds with a packet to inform the sender that the “destination was unreachable”.
When huge numbers of UDP packets are sent to server, server received and answered the packet, the system becomes overwhelmed and unresponsive to other clients. In this attack the attacker may also spoof the IP address of the packets to make sure that the return packets don’t reach their host, and to hide the attack. When the attack traffic comes from multiple devices, the attack becomes a DDoS or distributed denial-of-service attack.
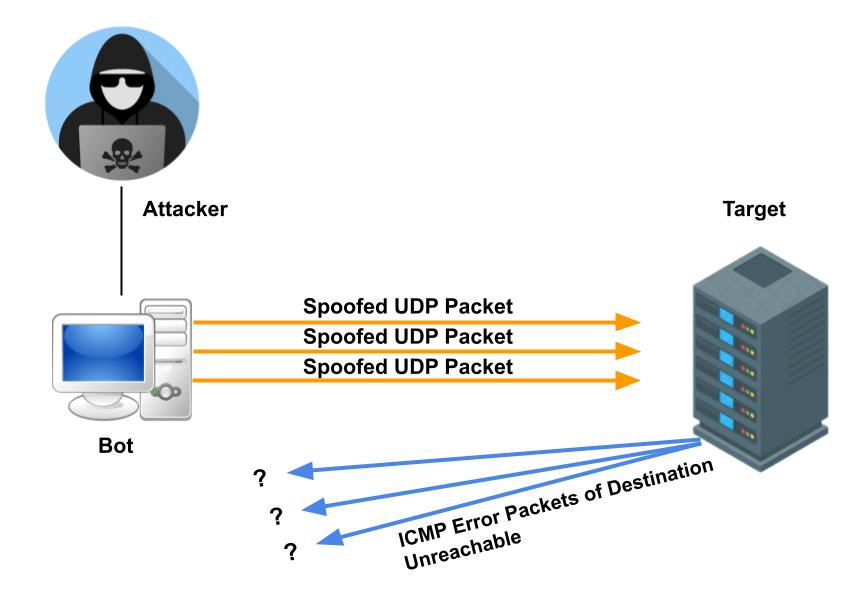
2. ICMP Flood
Internet Control Message Protocol (ICMP) flood attack is a denial-of-service attack, also known as Ping Flood attack. In this attack attacker send large number of ICMP echo-request(ping) packets to a targeted device and causing the target to become inaccessible. When the attack traffic comes from multiple devices, the attack becomes a DDoS or distributed denial-of-service attack.
Basically, a ping request tests the connectivity of two computers over a network by measuring the turnaround time between an ICMP(ping) request and its corresponding response. But In ping attack, attacker floods the victim’s network with request packets where the network has to respond with an equal number of reply packets. And this request-response game keeps the network channel busied for the entire duration of the ICMP attack, consuming significant bandwidth which results in a denial of service for a legitimate user.
3. SYN Flood
SYN flood is a denial-of-service attack, In which attacker initiates multiple TCP sessions but never completes the 3 way handshake. Under normal operation of 3 way handshake 3 distinct process is executed to make connection.
- Client/user sends a SYN packet to the server in order to initiate the connection.
- Server then responds to that initial packet with a SYN/ACK packet, in order to acknowledge the communication with user.
- Finally, the client returns an ACK packet to acknowledge the receipt of the packet from the server.
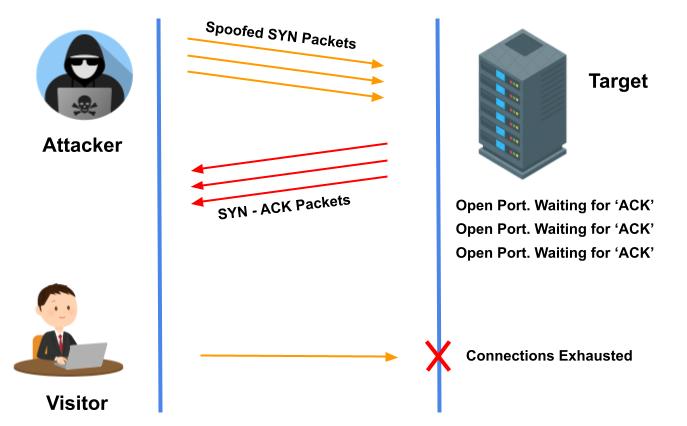
In SYN flood attack, the attacker sends repeated SYN packets to every port on the server, often using a spoof IP address. And server responds to each packet with a SYN-ACK packet from each open port. IP address is spoofed so server will never receive the responses of SYN-ACK packet, the server under attack will wait for acknowledgement of its SYN-ACK packet.
4. Smurf Attack
A smurf attack is a form of distributed denial of service (DDoS) attack that occurs at the network layer. Smurfing attacks are named after the malware DDoS.Smurf, which enables hackers to execute them. Smurf attack is very similar to ping flood attack, In which attacker sends an ICMP Echo request packets to server so that it become inaccessible by its user. Unlike the ping flood attack, Smurf is an amplification attack vector that amplifies its damage potential by exploiting characteristics of broadcast networks.
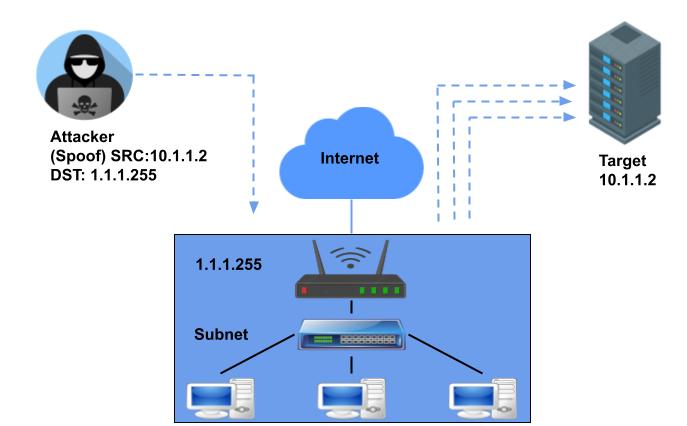
In Smurf attack, (1.) Smurf malware builds a spoofed packet that has its source address set to the real IP address of the targeted server. (2.) Then this packet is sent to an IP broadcast address of a router or firewall, which in turn sends requests to every host device address inside the broadcasting network. (3.) Each device inside the network receives the request from the broadcaster and then responds to the spoofed address of the target with an ICMP Echo Reply packet. (4.) The target server then receives a huge number of ICMP Echo Reply packets and potentially becoming overwhelmed and resulting inaccessible by its legitimate traffic/user.
5. Ping of Death
Ping of Death (PoD) is a form of Denial of Service (DoS) attack in which an attacker trys to freeze, destabilize, or crash the targeted computer/server or service by sending an oversized packets using a simple ping command. ICMP echo or ping is used to test a network connection, If the connection is working fine, then source device receives a reply from the targeted machine. The size of an Internet Protocol Version 4 (IPv4) packet including the IP header is 65,535 bytes, including a total payload size of 84 bytes.
When a maliciously large size packet is transmitted from the attacker to the target system, the packet becomes fragmented into segments(small piece of data), When the target system try to reassemble the fragments and ends up with an oversized packet, memory overflow could occur and causing the target system to crash, freeze or reboot. Old computer system cannot handle large size packets and easily vulnerable to this attack but modern computer systems are not vulnerable to ping of death attack.
6. Fragmented Attack
Also known as teardrop attack is a kind of denial-of-service (DoS) attack, In it, an attacker sends fragmented data packets to the target device/server and the server is unable to reassemble the packet, causing overload.
In normal IP fragmentation a large packets are broken apart into small packets called fragments, then transmitted across a network, and finally reassembled into the original packets as part of normal communications.
But in teardrop attack, when target machine receiving such packets cannot reassemble them due to a bug in TCP/IP fragmentation reassembly or fake fragments that cannot be defragmented submitted by attacker as a result the packets overlap one another, crashing the target machine
7. Slowloris
Slowloris is an application layer DDoS attack. Developed by Robert “RSnake” Hansen, In which attacker uses partial HTTP requests to open connections between a single computer and a targeted Web server, with none ever being completed and keeping those connections open for as long as possible, When the server’s maximum possible connections has been exceeded, each additional connection will not be answered and result denial-of-service will occur.
8. HTTP Flooding
HTTP flood attack is type of application layer Distributed Denial of Service (DDoS) attack. This attack is designed to overwhelm web servers’ resources by continuously http requesting from many source attacking machines called botnet. HTTP flood uses GET or POST requests to attack a web server or application.
- HTTP GET attack: In this attack, multiple computer or botnets are coordinated to send multiple http requests for images, files, or some other resources from a targeted server. Web server cannot handle huge amount of incoming requests and responses, result denial-of-service will occur.
- HTTP Post attack: when a form is submitted or comment is published on a website, the server must handle the incoming request and push or publish the data into a database. Huge amount of processing power and bandwidth required to send the POST request. So attacker sending many post requests directly to a targeted server until it’s capacity is reached and denial-of-service occurs.


Usually I do not learn post on blogs, but I would like to
say that this write-up very compelled me to try and do it!
Your writing style has been amazed me. Thank
you, quite great post.
Wow, great blog article.Really looking forward to read more. Will read on…
It’s hard to find well-informed people in this particular topic, however, you sound like you know what
you’re talking about! Thanks
I just could not leave your website prior to suggesting that I really enjoyed the standard information an individual provide to your
guests? Is going to be back ceaselessly to investigate cross-check new posts