What Is Asymmetric Key Cryptography ?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. Sender uses first key (public key) to encrypt the message and receiver uses second key (private key) to decrypt the message. Unlike private key cryptography, if one key is used to encrypt, that same key cannot decrypt the message. The private key should not be distributed & should remain with the owner only, while the public key can be used by anyone.
Many protocols rely on asymmetric key cryptography, including the transport layer security (TLS) and secure sockets layer (SSL) protocols, which make our browsing over the internet secure. Public key cryptography provide key distribution and secrecy (e.g., Diffie–Hellman key exchange), some provide digital signatures (e.g., Digital Signature Algorithm), and some provide both (e.g., RSA).
Two of the best-known uses of asymmetric key cryptography are:
1. Public key encryption

Public key encryption uses a mathematically related pair of keys public for encryption and private for decryption. Let’s understand with an example- Aman is sender and Tarun is recipient both has its own pair of public and private keys. First, Aman obtains the Tarun’s public key. Then Aman encrypt the plain text message by using Tarun’s public key. This encrypted text is sent to the Tarun, who decrypts it with their private key, returning it to legible plaintext. This can be used to ensure confidentiality of a message.
2. Digital signatures
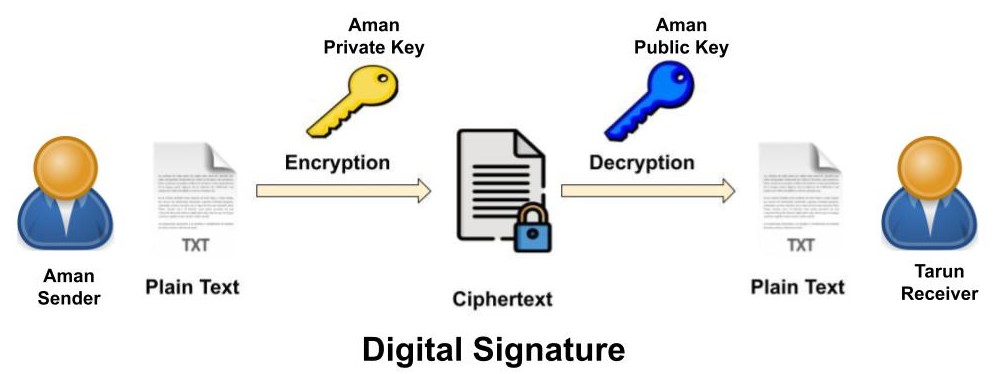
Asymmetric key cryptography is also used for authentication data using digital signatures. In this message is signed with the sender’s private key (Aman) and can be verified by anyone who has access to the sender’s public key. A digital signature is a mathematical method used to validate the authenticity & integrity of a message or digital document. This also ensures that the message has not been tampered. Digital signatures are widely used today for signing digital contracts, for authorizing bank payments and signing transactions in the public blockchain systems for transferring digital assets.
Most widely used asymmetric key algorithms are
- Diffie-Hellman (DH)
- RSA (Rivest, Shamir, Adleman)
- Elliptic Curve Cryptography (ECC)
- Digital Signature Algorithm/Standard (DSA/DSS)
What is Diffie-Hellman (DH)?
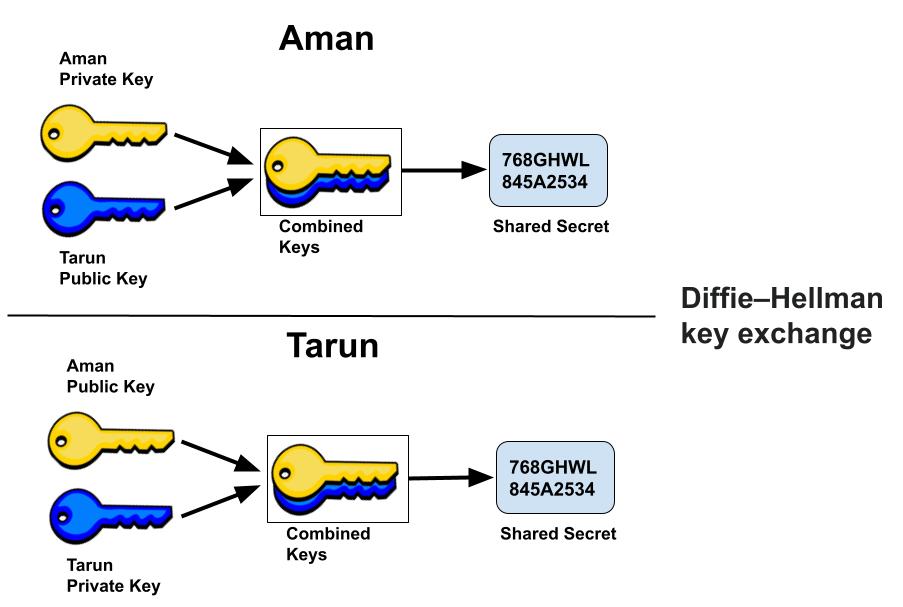
Diffie Hellman (DH) key exchange algorithm is a method for securely exchanging cryptographic keys over a public communications channel. The Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure channel. Keys are not actually exchanged – they are jointly derived. Diffie Hellman key exchange algorithm can be used for only key exchange, not for encryption and decryption process. DH is generally explained by two sample parties, Aman (Sender) and Tarun (Receiver), initiating a dialogue. Both party generates a public/private key pair and distributes the public key. After obtaining an authentic copy of each other’s public keys, Aman and Tarun can compute a shared secret offline. The shared secret can be used, for instance, as the key for a symmetric cipher. Since it doesn’t authenticate any party in the transmission, so the Diffie Hellman key exchange is susceptible to a man-in-the-middle attack.
What is RSA (Rivest, Shamir, Adleman)?
The RSA algorithm is an asymmetric cryptography algorithm, uses two different but mathematically linked keys –one public and one private. The Public key is used for encryption, and the Private Key is used for decryption. The public key is well known and shared publicly, but the private key is secret and it is known only to the user who owns the key and must not be shared with anyone. This algorithm was invented by Rivest, Shamir and Adleman in year 1978 that’s why name RSA algorithm.
In RSA algorithm, public key consists of two numbers where one number is multiplication of two large prime numbers. And private key is also derived from the same two prime numbers. Encryption strength totally depends upon the key size and if we increase the key size, the strength of encryption increase and the size of key is 1024 or 2048 bits. RSA is widely used in Virtual Private Networks (VPNs), email services, web browser (TLS), digital signing for code and certificates. Certificates can be used to verify the public key’s owner, by signing it with the private key of the key pair owner.
What is Elliptic Curve Cryptography (ECC)?
Elliptic-curve cryptography (ECC) is a public-key cryptography based on the mathematics structure of elliptic curves. ECC implements all major capabilities of the asymmetric cryptosystems like key exchange, signatures and encryption. ECC cryptography is considered a modern successor of the RSA cryptography. Because ECC has smaller keys size and signatures as compared to RSA algorithm and provide same level of security, also provides very fast key generation & fast key agreement. ECC generates public/private keys through the properties of an elliptic curve equation instead of the traditional method of generation as the product of large prime numbers. In RSA cryptography, where both keys are integers, while in ECC the private and public keys are not equally exchangeable. Instead the public key is a point on the curve, while the private key is still an integer.
How to Protect Keys in cryptography?
In Cryptography the only things that should be “secret” when it comes to a secure Communication are the keys themselves. Never store encryption/decryption keys in plain text along with the data that they protect. The most common methods for protecting keys are
- Always Store keys in a filesystem and protect them with strong access control lists (ACLs).
- Always encrypt your encryption keys with a second key encrypting key (KEK). The KEK should be generated using password-based encryption.
- Hardware Security Module (HSM) is an appliance for generating and storing cryptographic keys that is less susceptible to tampering than software based storage.
Learn More About Cryptography
- What is Cryptography?
- What is Symmetric Key Algorithm?
- What is Data Encryption Standard (DES)?
- What is Advanced Encryption Standard (AES)?
Related Topics
1. What is an IP address?
2. Difference between IPv4 & IPv6.
3. Difference between Public and Private IP Address.
4. What is DHCP Server?
5. What Is DORA Process in DHCP?
6. What is DNS Server and How Its work?
7. What is Ports and Protocols in computer networks?
8. How Proxy Server hides IP Addresses?
9. What is Firewall?
10. How DNS Server related to IP Address?
11. IDS Vs IPS in Security.
12. Difference between Hub, Switch & Router.