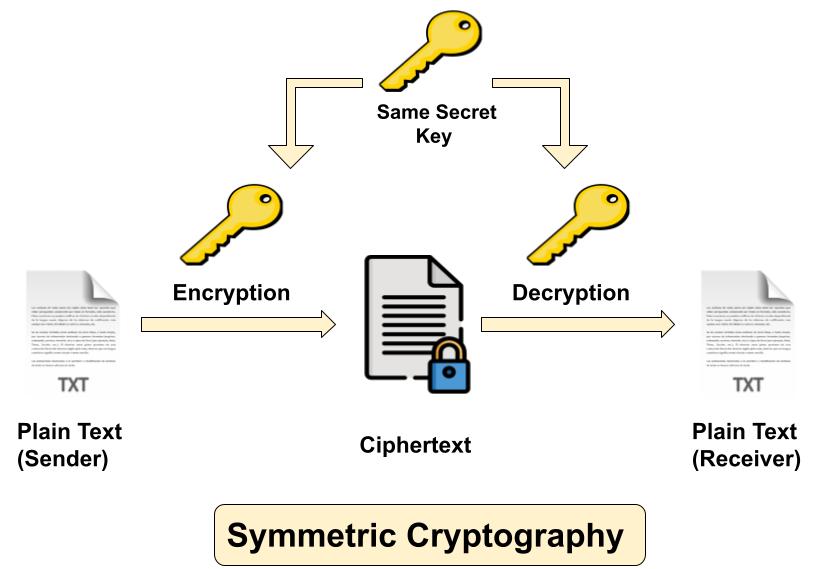
Symmetric key cryptography
Symmetric Key Cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message. Symmetric key cryptography can be used on in-transit, at-rest and in-use data, but it is commonly only used on at-rest data, as sending the secret to the receiver of the message can lead to compromise. Confidentiality can be assured with symmetric encryption but key distribution can be challenging with it.
Most famous symmetric algorithms are
- Data Encryption Standard (DES)
- Triple DES (3DES)
- Advanced Encryption Standard (AES)
- International Data Encryption Algorithm (IDEA)
- Blowfish and Twofish
- Rivest Cipher (RC)
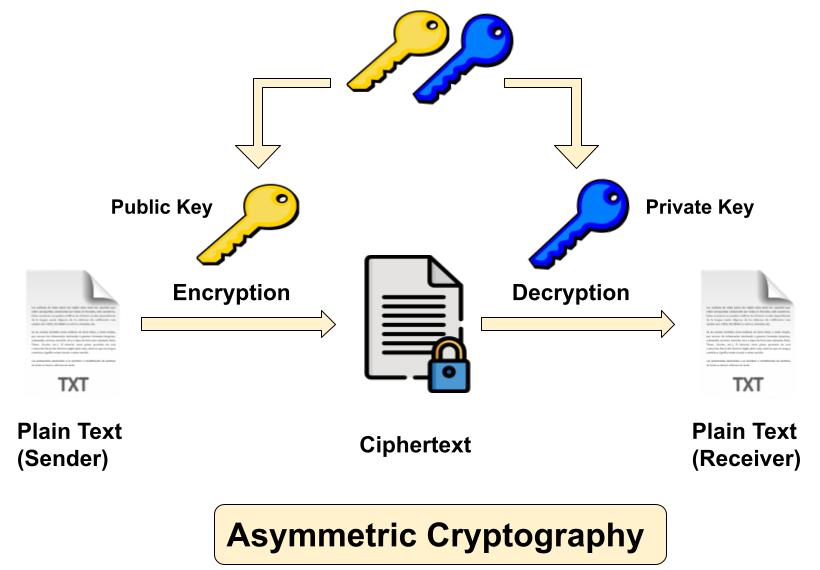
Asymmetric Key Cryptography
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. Sender uses first key (public key) to encrypt the message and receiver uses second key (private key) to decrypt the message. Unlike private key cryptography, if one key is used to encrypt, that same key cannot decrypt the message. The private key should not be distributed & should remain with the owner only, while the public key can be used by anyone.
Many protocols rely on asymmetric key cryptography, including the transport layer security (TLS) and secure sockets layer (SSL) protocols, which make our browsing over the internet secure. Public key cryptography provide key distribution and secrecy (e.g., Diffie–Hellman key exchange), some provide digital signatures (e.g., Digital Signature Algorithm), and some provide both (e.g., RSA).
Most famous symmetric algorithms are
- Diffie-Hellman (DH)
- RSA (Rivest, Shamir, Adleman)
- Elliptic Curve Cryptography (ECC)
- Digital Signature Algorithm/Standard (DSA/DSS)
Difference between Symmetric and Asymmetric key cryptography
| Parameters | Symmetric Key Cryptography | Asymmetric Key Cryptography |
| Name | It is also popular as private key cryptography | It is also popular as public key cryptography |
| Number of keys | Sender and Receiver both use a single key to encrypt and decrypt the data | Sender and Receiver both use two keys to encrypt and decrypt the data |
| Key used | For encryption – Private key is used For decryption – Private key is used | For encryption – Public key is used For decryption – Private key is used |
| Key Length | Symmetric cryptography uses smaller key size 128-Bits | Asymmetric cryptography uses smaller key size 1024-Bits |
| Speed | The encryption and decryption process is very fast. | The encryption and decryption process is very slow |
| Data Size | It is used for bulk transmission of data | It is used for small amount of transmission of data |
| Confidentiality | It only provides confidentiality. | It focuses on confidentiality, authenticity and non-repudiation |
| Resource Utilization | Symmetric cryptography utilizes less resource as compared to asymmetric cryptography | In asymmetric cryptography, resource utilization is high. |
| Efficiency | It utilizes less resource as a result its efficiency increases | It is less efficient as compared to symmetric cryptography |
| Techniques | Symmetric key is old and outdated technique | While asymmetric key is a modern and new in cryptography |
| Security | Due to old techniques and small key size, it is insecure | Highly secured due to large key size |
| Implement | Symmetric cryptography is easy to implement compared to asymmetric cryptography | Asymmetric cryptography is difficult to implement |
| Use Cases | It is widely used in Banking and Data Storage | It is widely used in Digital Signing and Blockchain |
| Famous Algorithms | 1. Data Encryption Standard (DES) 2. Triple DES (3DES) 3. Advanced Encryption Standard (AES) 4. International Data Encryption Algorithm (IDEA) 5. Blowfish and Twofish 6. Rivest Cipher (RC) | 1. Diffie-Hellman (DH) 2. RSA (Rivest, Shamir, Adleman) 3. Elliptic Curve Cryptography (ECC) 4. Digital Signature Algorithm/Standard (DSA/DSS) |
Advantages and Disadvantages of Symmetric cryptography
- A Symmetric key cryptography is more effective.
- A message can only be decrypted by a device that has a secret key.
- Key transportation is a concern in symmetric key cryptography. The secret key must be sent to the recipient before the final message is sent.
- In Symmetric key cryptography digital signatures is not possible so message’s origin and validity cannot be assured.
- In symmetric key cryptography, no one can guarantee the communication networks will not be tapped.
Advantages and Disadvantages of Asymmetric cryptography
- Asymmetric key cryptography use of digital signatures so Message verification is possible in public-key cryptography.
- Digital signature helps the recipient to determine whether the message was altered or tapped during transit.
- Signing a message digitally is analogous to physically signing a document. Since it is an acknowledgement of the message, the sender cannot reject it.
- It consumes more computer resources. It necessitates much more computing resources than single-key encryption.
- If the hacker obtains a sender or receiver’s private key then security breach is happened.
Learn More About Cryptography
- What is Cryptography?
- What is Symmetric Key Algorithm?
- What is Public Key Cryptography?
- What is Digital Signature?
- What is Data Encryption Standard (DES)?
- What is Advanced Encryption Standard (AES)?
Related Topics
1. What is an IP address?
2. Difference between IPv4 & IPv6.
3. Difference between Public and Private IP Address.
4. What is DHCP Server?
5. What Is DORA Process in DHCP?
6. What is DNS Server and How Its work?
7. What is Ports and Protocols in computer networks?
8. How Proxy Server hides IP Addresses?
9. What is Firewall?
10. How DNS Server related to IP Address?
11. IDS Vs IPS in Security.
12. Difference between Hub, Switch & Router.