What Is Kerberos?
Kerberos is the computer network authentication protocol that is used to verify the identity of a user. Initially Kerberos is developed in the 1980s by Massachusetts Institute of Technology (MIT) Computer Engineers. Now Kerberos authentication protocol is the default authorization protocol used by Microsoft Windows and it is an integral part of the Windows Active Directory (AD) service. Kerberos authentication protocol also implement in Apple OS (Mac OS), Linux, UNIX, and FreeBSD. Microsoft rolled out its version of Kerberos in Windows 2000, and it’s become the go-to protocol for websites and single sign-on implementations over different platforms.
Kerberos is a more secure authorization protocol as compared to previous authorization technologies. The strong symmetric cryptography and third-party ticket authorization make it much more difficult for hackers or intruders to infiltrate your network. Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC).
Why Microsoft made Kerberos as a default authentication protocol?

Before Kerberos authentication protocol, Microsoft was using NTLM authentication technology for authentication. NTLM stands for NT LAN Manager and is a challenge-response authentication protocol. In NTLM, the target server or domain controller challenge and check the password, and store password hashes for continued use. And the major reason, Microsoft preferred Kerberos as a default authentication protocol was third-party verification and stronger encryption capability in Kerberos. These extra steps provides a significant additional layer of security over NTLM. NTLM simply older technology, and you shouldn’t rely upon NTLM to protect sensitive data.
Kerberos Terminologies
- Client: The client acts on behalf of the user and initiates communication for a service request.
- Server: The server hosts the service (may be webserver or application server) the user wants to access.
- Key Distribution Center (KDC): Key distribution center (KDC), which acts as Kerberos’ trusted third-party authentication service. In a Kerberos environment, the authentication process is separated into three parts: A database (db), the Authentication Server (AS), and the Ticket Granting Server (TGS).
- Authentication Server (AS): The AS performs the desired client authentication. And AS checks to see if the client is in its database. If the client is found in database, authentication happens successfully, the AS issues the client a ticket called TGT (Ticket Granting Ticket). This ticket assures the other servers that the client is authenticated.
- Ticket Granting Server (TGS): This Kerberos server accepts the TGT(Ticket Granting Ticket) so that clients can access their application servers.
How Does Kerberos Authentication Work?
A simplified description of how Kerberos works mention below; the actual process is more complicated and may vary from one implementation to another:
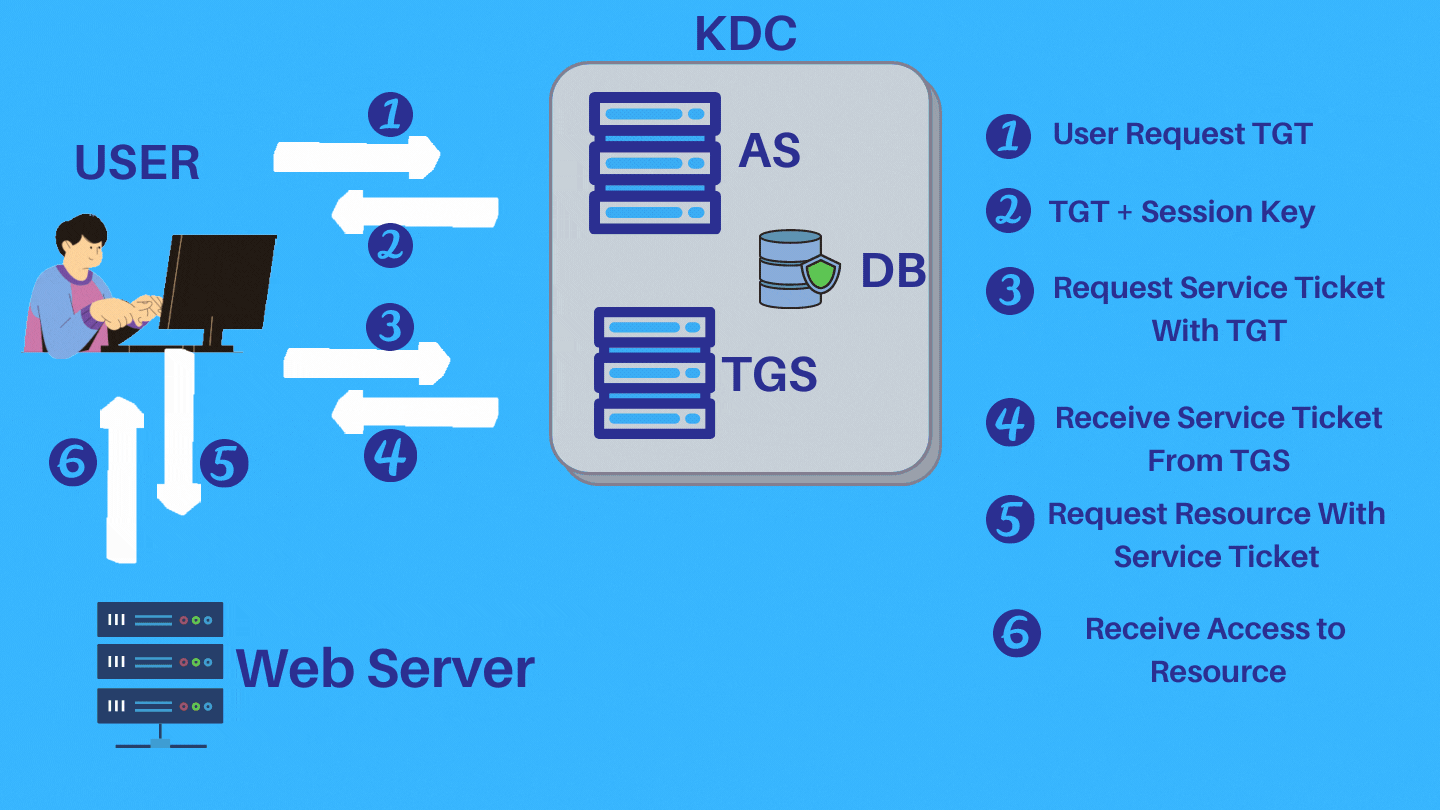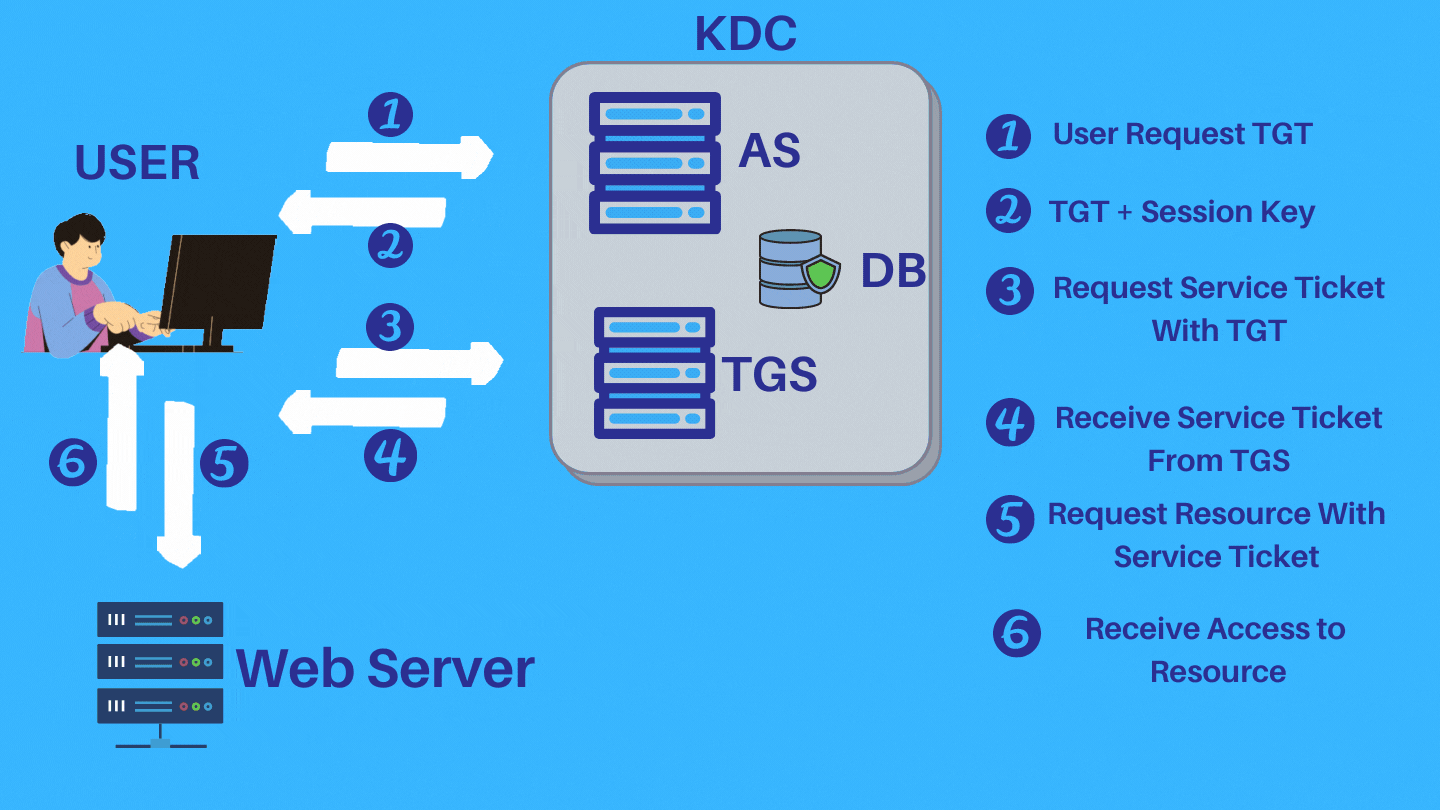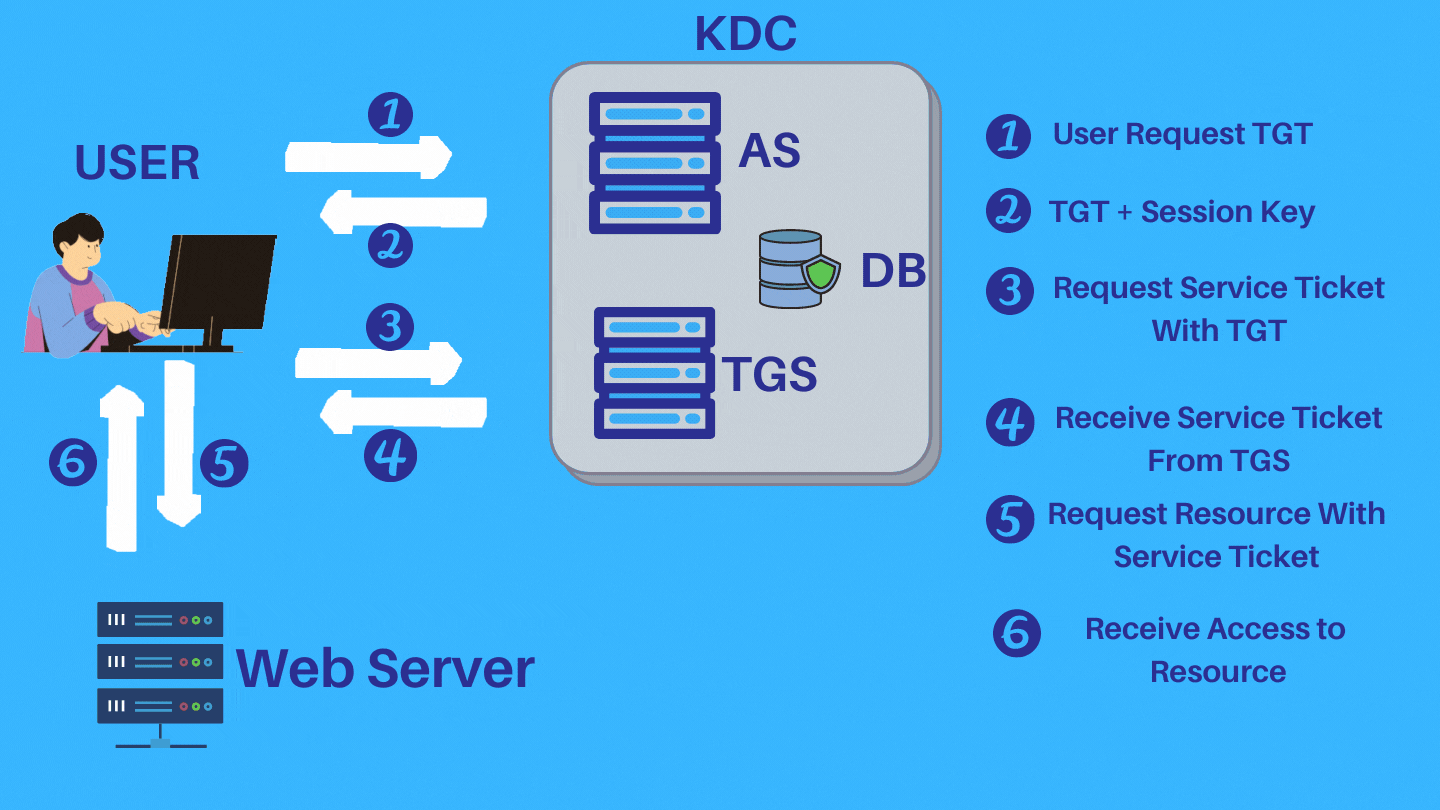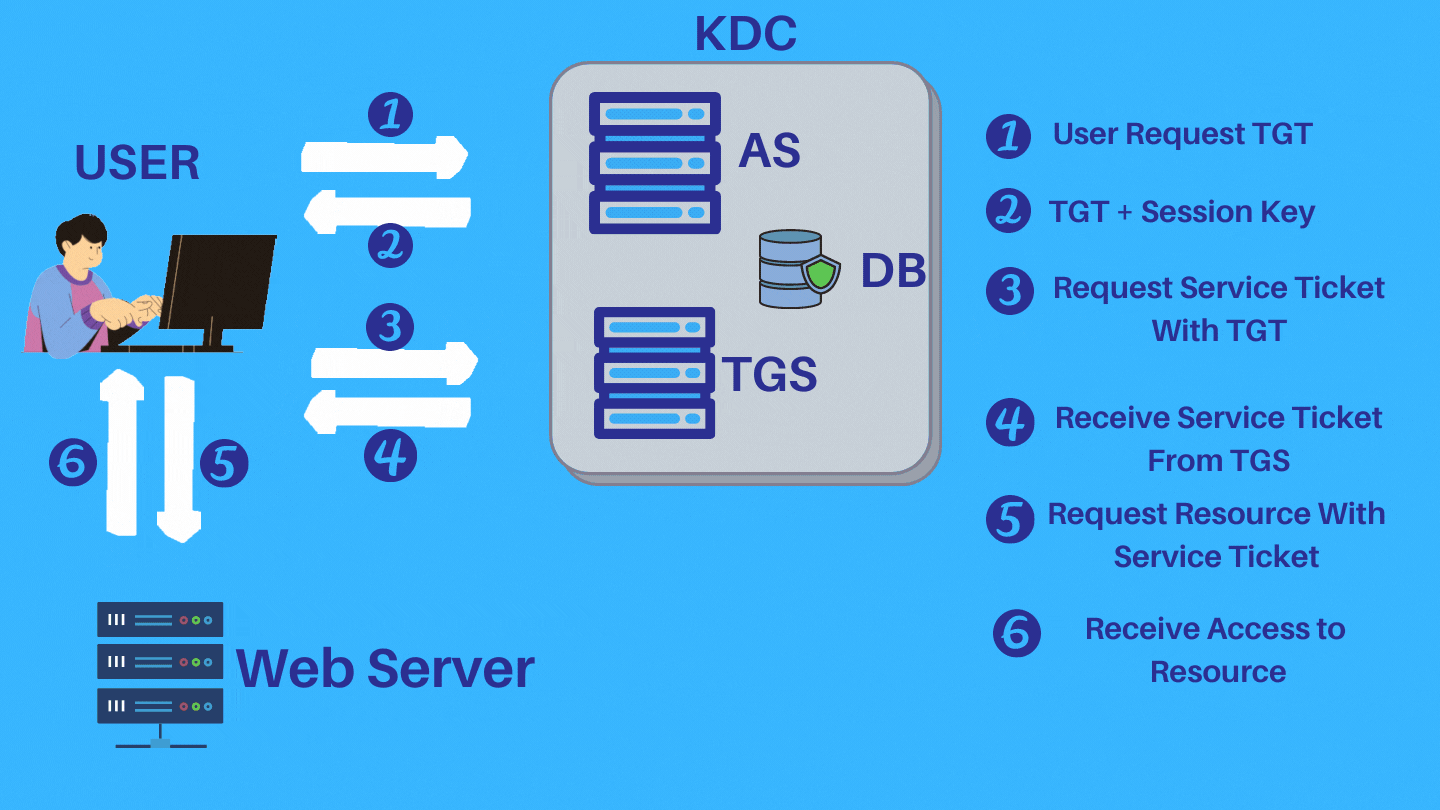
Step 1: To start the Kerberos authentication process, first client enter their credentials (only userID), sends an authentication request to the Kerberos Key distribution center (KDC)’s authentication server. The authentication server verifies that the client’s username is in the KDC database.
Step 2: If the client’s username isn’t available in the KDC database, the client cannot be authenticated, and the authentication process ends. If client’s username or userID is found in KDC database, the authentication server sends the client a Ticket Granting Ticket (TGT) and a session key (SK1). TGT containing the client ID, client network address, timestamp and lifetime. Session key (SK1) is encrypted by client’s secret key and TGT is encrypted by using the secret key of the TGS.
Step 3: The client uses the client/user secret key (generated from the password entered by the user) to decrypt the message and extract the Session key and TGT. After decrypting it, This session key is used for further communications with the TGS.
Step 4: After authenticated by authentication server and decrypt the session key, the client asks for a service ticket (for web/application server access) from the Ticket Granting Server (TGS).
Step 5: The TGS then uses the TGS secret key to decrypt the TGT received from the client and extracts the session key (SK1). TGS decrypts the authenticator (TGT) and checks to see if it matches the client’s username and client network address. The TGS also uses the extracted timestamp to make sure the TGT hasn’t expired. If the process conducts all the checks successfully, then the KDC generates a service session key (SK2) that is shared between the client and the target server (which may be web server or application server).
Step 6: The client sends a request to access the application server. This request includes the service session key (SK2) received previous step by TGS. If the application server can authenticate this request, the client can access the server.
Is Really Kerberos Authentication Invulnerable?
There is no security model which is completely invulnerable, not even Kerberos. Kerberos is widely used authentication protocol from last two decade, hackers have found ways to get around it. Hacker uses many techniques to hack the Kerberos authentication protocol.
1. Brute force attack
An automated and continued attempt at guessing a user’s password. In this attack hacker try to all possible combination of password space. By using this attack, hackers target the ticket-granting and initial ticketing service.
2. Pass the ticket
An attacker forges the session key and uses fake credentials. Hackers usually forge a golden ticket (a ticket that grants domain admin access) or a silver ticket (a ticket that grants access to a service).
3. Pass the key
It is the form of pass-the-hash attack in which attackers impersonate authorized users by replaying their credentials. In this attacker to authenticate to server or service by using the hash instead of requiring the associated plaintext password.
4. DCShadow Attack
DCShadow allows an attacker with enough privileges to create a rogue Domain Controller and push changes to the DC Active Directory objects. It occurs only when attackers gain enough access within the network to set up their own DC.
Major Advantages & Disadvantages of Kerberos Authentication
The major advantages in adopting Kerberos as an authentication protocol are given below:
- Mutual authentication, Kerberos authentication allows server systems and users to authenticate each other. During all steps of the process, the user and the server will know that the counterparts that they are interacting with are authentic.
- In Kerberos authentication process, Passwords are never sent across the network because only keys are sent in an encrypted form.
- Limited Ticket Lifetime means Each ticket in Kerberos has timestamps and lifetime data, and the duration of authentication is controlled by admins.
- Kerberos authentication is reusable, Each user will only have to be verified by the system once. Then throughout the lifetime of the ticket, the user can authenticate without the need to re-enter personal information.
- Kerberos uses multiple secret keys, third-party authorization, and symmetric key cryptography make it more secure as compared to others authentication protocols.
Kerberos uses strong cryptography, including secret-key encryption, to protect sensitive data but it does not means it can’t be hack. Kerberos have some weakness mention in below:
- If a hacker got the access to the Key Distribution Center, the whole authentication system is compromised.
- Kerberos requires user accounts and services to have a trusted relationship to the Kerberos token server.
- Kerberos uses symmetric cryptography Data Encryption Standard (DES) but is no longer an Internet standard because it is weak. And still Kerberos have not been updated to newer ciphers like Advanced Encryption Standard (AES).

