Data Encryption Standard (DES) and Advanced Encryption Standard (AES) are the symmetric block cipher. Before learning DES vs AES, let’s understand what is symmetric cryptography and block cipher?
Symmetric key cryptography also known as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message. And a block cipher is an encryption technique that breaks down plaintext messages into fixed-size blocks then converts one block of the message at a time. Block cipher is used for database, file encryption. It is an implement through a software solution.
DES vs AES with comparison table
| Parameters | DES Algorithm | AES Algorithm |
| Full Form | DES stands for Data Encryption Standard | AES stands for Advanced Encryption Standard |
| Structure | DES structure is based on feistal network | AES structure is based on substitution-permutation network. |
| Size of Key | The size of key length is of 56 bits | While in key length varies from 128 bits, 192 bits to 256 bits. |
| Number of rounds | DES involves 16 rounds of identical operations | In AES Number of rounds depends on key length 128 bits – 10 Round 192 bits – 12 Round 256 bits – 14 Round |
| Block Size | The block size is 64 bits in DES | Block size can be of 128, 192, or 256 bits – depending upon the key length. |
| Designed By | DES was designed by IBM. And sstablished as a standard in 1977. | AES was designed by Vincent Rijmen and Joan Daemen and standardized in 2001. |
| Security | DES can be broken easily as it has known vulnerabilities. And due to smaller key, which make it less secure. | AES is more secure than the DES cipher due to larger key size. |
| Speed | The encryption process is time-consuming | While AES offers almost six times faster performance compared to DES. |
| Encryption | An encryption round involves Expansions permutation Xor, S-box, P-box, Xor, and Swap. | Encryption round involves Subtypes, Shiftonce, Mix columns, and Addroundkeys. |
| Known Attacks/Vulnerabilities | DES is vulnerable to a differential, and Brute Force attacker could be analyzed plaint text using differential cryptanalysis. | It is strong against differential, shrank differential linear interpolation and square attacks |
Data Encryption Standard (DES) algorithm
The Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption designed by an IBM team and published by the National Institute of Standards and Technology (NIST). It is symmetric key cryptography, so it uses the same key to encrypt and decrypt a message and key length is 56 bits. DES is a block cipher and encrypts data in blocks size of 64 bits each, which means 64 bits of plaintext goes as the input to DES, and produces 64 bits of cipher text.
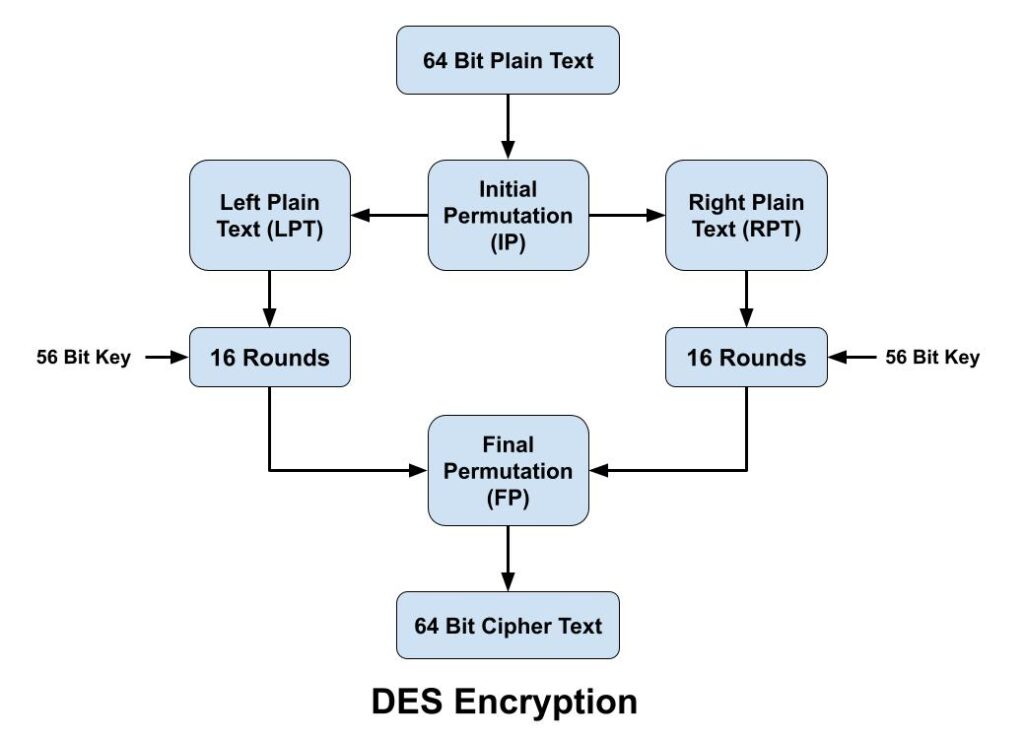
The DES algorithm encryption process breaks down into the following steps:
- In first step, the 64-bit plain text block is handed over to an initial Permutation (IP) function.
- Initial permutation (IP) is then performed on the given plain text.
- The IP produces two halves of the permuted block, known as Left Plain Text (LPT) and Right Plain Text (RPT).
- Both LPT and RPT go through 16 rounds of the encryption process.
- Finally, both LPT and RPT are recombined, and a Final Permutation (FP) is performed on the newly combined block.
- Finally 64-bit cipher text is produced.
Advanced Encryption Standard (AES)
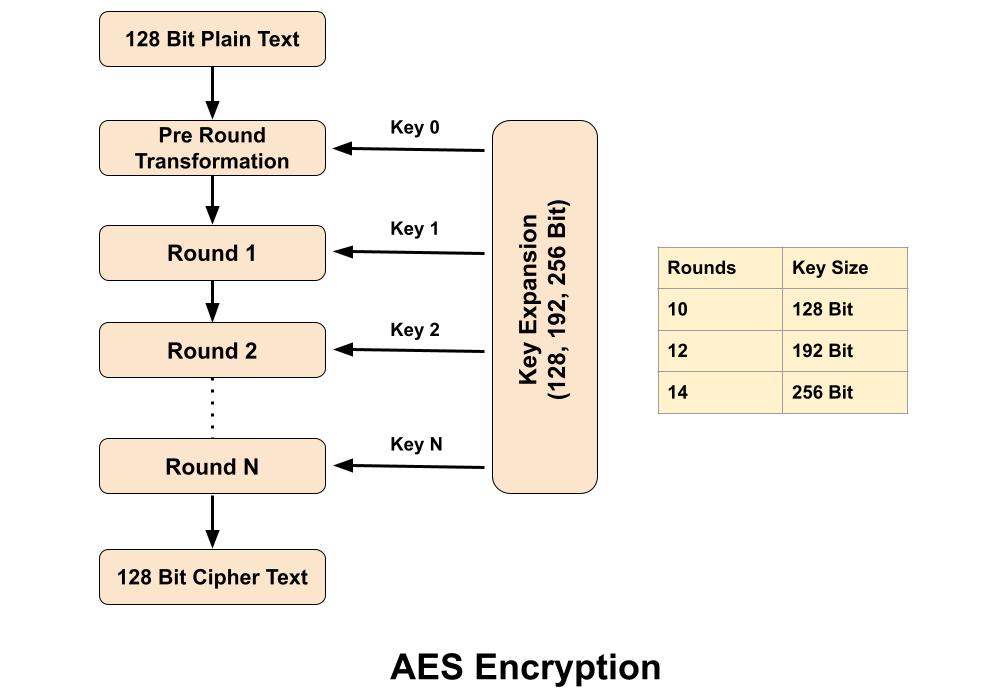
The Advanced Encryption Standard (AES) algorithm is a symmetric-key block cipher (block size 128 bit) encryption designed & by published by the National Institute of Standards and Technology (NIST) in 2001. AES is widely used today as it is a much stronger than DES and 3DES. In Advanced Encryption Standard number of rounds depends on the key length, 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys. Advanced Encryption Standard takes 128 bits plain text as input and produced 128 bits cipher text as output. It’s encryption process is based on a substitution-permutation network, also referred as an SP network. It consists of a series of linked operations, including replacing inputs with specific outputs (substitutions) and others involving bit shuffling (permutations).
Conclusion
Both DES and AES are used for encryption of the data and are useful in their own way. AES came as the successor of DES to overcome its drawbacks. DES is the older algorithm and AES is the advanced algorithm which is faster and more secure than DES. That’s why all modern day applications rely on AES instead of the DES algorithm for secure encryption. Although DES had made great contributions in the field of data security, but now it is replaced by AES in the areas of high security.
Related Questions & Answers
1 What is cryptography?
Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information, so that only those for whom the information is intended can read and process it. In information Read more
2 What is Private Key Cryptography?
Symmetric cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message… Read more
3 What is Public Key Cryptography?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. he private key should not be… Read more
4 Difference between Stream & Block Cipher?
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Both Stream Cipher and Block Cipher are…Read more
Related Topics
1. What is an IP address?
2. Difference between IPv4 & IPv6.
3. Difference between Public and Private IP Address.
4. What is DHCP Server?
5. What Is DORA Process in DHCP?
6. What is DNS Server and How Its work?
7. What is Ports and Protocols in computer networks?
8. How Proxy Server hides IP Addresses?
9. What is Firewall?
10. How DNS Server related to IP Address?
11. IDS Vs IPS in Security.
12. Difference between Hub, Switch & Router.

You explained well working of DES but could you elaborate more AES. Still i m little bit confused.