What is Information Security ?
Information Security sometimes called InfoSec, act of protecting data and information from unauthorized access, unlawful modification and disruption, disclosure, corruption, and destruction. Information security’s primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity.
CIA TRIAD
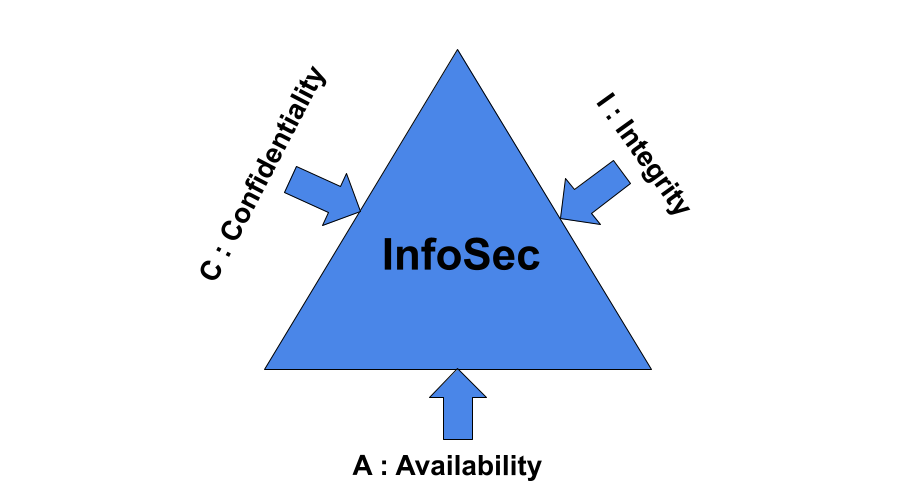
- Confidentiality: makes sure that only authorized personnel are given access or permission to modify data. And Information has not been disclosed to unauthorized people.
- Integrity: means information has not been modified or altered without proper authorization. It helps maintain the trustworthiness of data by having it in the correct state and immune to any improper modifications.
- Availability: means that the authorized users should be able to access data whenever required. In other words Information is able to be stored, accessed, or protected at all times
The CIA Triad is so elementary to information security that anytime data violation or any number of other security incidents occur or security data breaches, it is definitely due to one or more of these principles being compromised. So, the CIA Triad is always on top of the priority list for any infosec professional.
AAA in Information Security
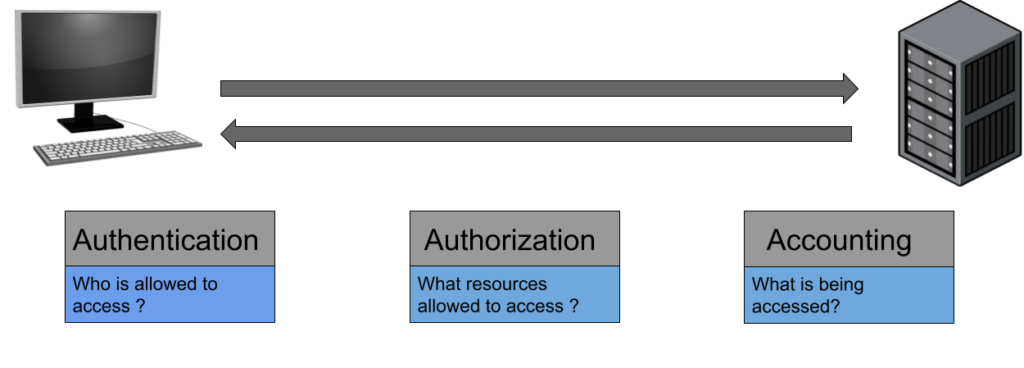
AAA (Authentication, Authorization, Accounting) is a system for tracking user activities on IP based network & controlling their access to network. AAA is implemented as dedicated server. In other words AAA is a framework for intelligently controlling access to computer resources, enforcing policies, auditing usage, and providing the information necessary to bill for services. These processes working in concert are important for effective network management and security.
- Authentication: When a person’s identity is established with proof and confirmed by a system. In Authentication user authenticate himself by one of these 5 methods.
● Something you know
● Something you are
● Something you have
● Something you do
● Somewhere you are
- Authorization: Occurs when a user is given access to a certain piece of data or certain areas of a building. Authorization is the process of enforcing policies—determining what types or qualities of activities, resources, or services a user is permitted. Usually authorization occurs within the context of authentication. After you have authenticated a user, they may be authorized for different types of access or activity.
- Accounting: The final piece in the AAA framework is accounting which track the data, computer usage, and network resources consumed by the user during access period. Accounting is carried out by logging session statistics and usage information. It is used for authorization control, billing, trend analysis, resource utilization, and planning for the data capacity required for business operations.
Security Threats
- Malware: Malware is malicious software or program designed to infiltrate a computer system/network and possible damage it without the user’s knowledge or consent.
- Unauthorized Access: Occurs when access to computer resources and data occurs without the consent of the owner.
- System Failure: Occurs when a computer crashes or an individual application fails. In corporate world system failure is major security threat, because it can shutdown whole business.
- Social Engineering: Act of manipulating users into revealing confidential information or performing other detrimental actions.
How to mitigate the Security Threats
- Physical Controls: By using physical things like alarm systems, locks, surveillance cameras, identification cards, and security guards. We can mitigate the threats.
- Technical Controls: By using smart cards, encryption, access control lists (ACLs), intrusion detection systems, Firewall, Intrusion prevention system and network authentication. We can mitigate the threats.
- Administrative Controls: By making policies, procedures, security awareness training, contingency planning, and disaster recovery plans. We can also mitigate the these security threats. User training is the most cost-effective security control to use
Read More
What is Malware and it Different types?
What is cybersecurity and its importance in today’s world?
Malware Exploitation & Techniques


what is the difference between cybersecurity and information security?
Very informative text thank you for sending.
I do not even know how I ended up here, but I thought this post was good. I don’t know who you are but certainly you’re going to a famous blogger if you aren’t already 😉 Cheers!
Great blog! Is your theme custom made or did you download it from somewhere? A design like yours with a few simple tweeks would really make my blog shine. Please let me know where you got your design. Bless you
Hello there! Do you know if they make any plugins to assist with SEO? I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good gains. If you know of any please share. Thank you!
Hi there to every body, it’s my first visit of this
blog; this website carries awesome and genuinely good information for readers.
Im obliged for the blog post.Really thank you! Fantastic.
You really make it seem so easy with your presentation but I find this topic to be
actually something which I think I would never understand.
It seems too complicated and very broad for me.
I’m looking forward for your next post, I’ll try to get the hang of it!
I love reading through an article that can make people think.
Also, many thanks for permitting me to comment!
Hello very cool web site!! Man .. Beautiful .. Amazing ..
I will bookmark your blog and take the feeds additionally?
I’m satisfied to seek out numerous helpful info
right here within the put up, we’d like work out more strategies in this regard, thanks
for sharing. . . . . .