Meaning of Cryptography
Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information, so that only those for whom the information is intended can read and process it. In information technology, It is the method used for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography is derived from the mathematics, computer science, electrical engineering, communication science, physics and a set of rule-based calculations called algorithms. These algorithms are used for cryptographic key generation, digital signing & verification to protect data privacy. These algorithms hard to break in actual practice by any adversary. In modern age cryptography is effectively synonymous with encryption, process of converting ordinary information (plaintext) into unintelligible form called ciphertext.
Cryptography focus on four main objectives
- Confidentiality: Information has not been disclosed to unauthorized people.
- Integrity: Information has not been modified or altered without proper authorization.
- Non-repudiation: The sender of information cannot deny his or her intention to send information at later stage.
- Authentication: The sender and receiver can confirm each other’s identity and the origin/destination of the information.
Types of Cryptography
Cryptography can be classified into three different types
- Symmetric Cryptography (Private Key Cryptography)
- Asymmetric Cryptography (Public Key Cryptography)
- Hash Function
Symmetric cryptography
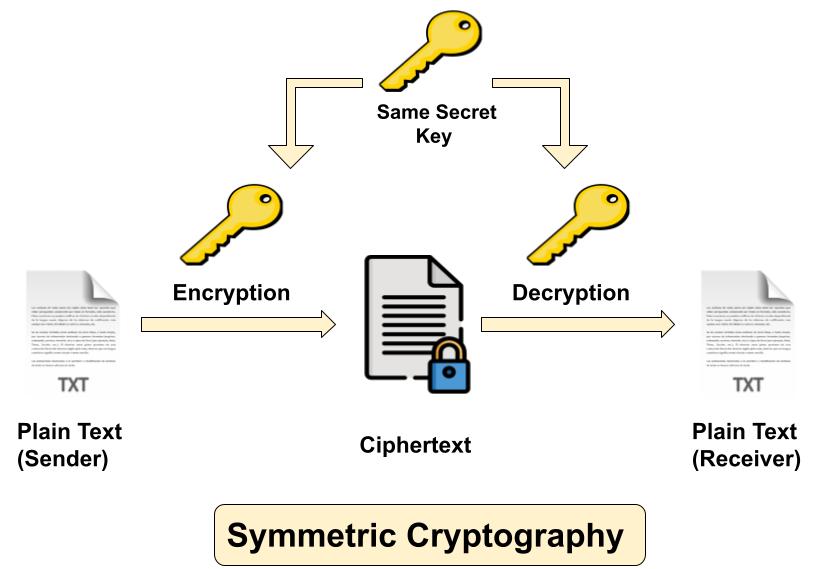
Symmetric cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message. Symmetric key cryptography can be used on in-transit, at-rest and in-use data, but it is commonly only used on at-rest data, as sending the secret to the receiver of the message can lead to compromise. Confidentiality can be assured with symmetric encryption but key distribution can be challenging with it. Most famous symmetric algorithms are
- Data Encryption Standard (DES)
- Triple DES (3DES)
- Advanced Encryption Standard (AES)
- International Data Encryption Algorithm (IDEA)
- Blowfish and Twofish
- Rivest Cipher (RC-4,5,6)
Asymmetric Cryptography
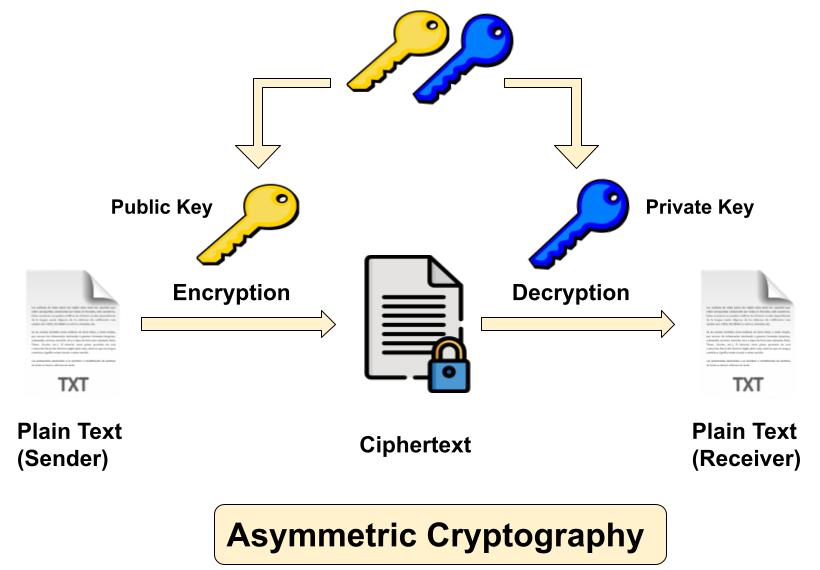
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One is used for encryption, while the other key is used for decryption. Sender uses first key (public key) to encrypt the message and receiver uses second key (private key) to decrypt the message. Unlike private key cryptography, if one key is used to encrypt, that same key cannot decrypt the message. The private key should not be distributed & should remain with the owner only, while the public key can be used by anyone. Most widely used asymmetric algorithms are
- Diffie-Hellman (DH)
- RSA (Rivest, Shamir, Adleman)
- Elliptic Curve Cryptography (ECC)
- Digital Signature Algorithm/Standard (DSA/DSS)
Hash Function
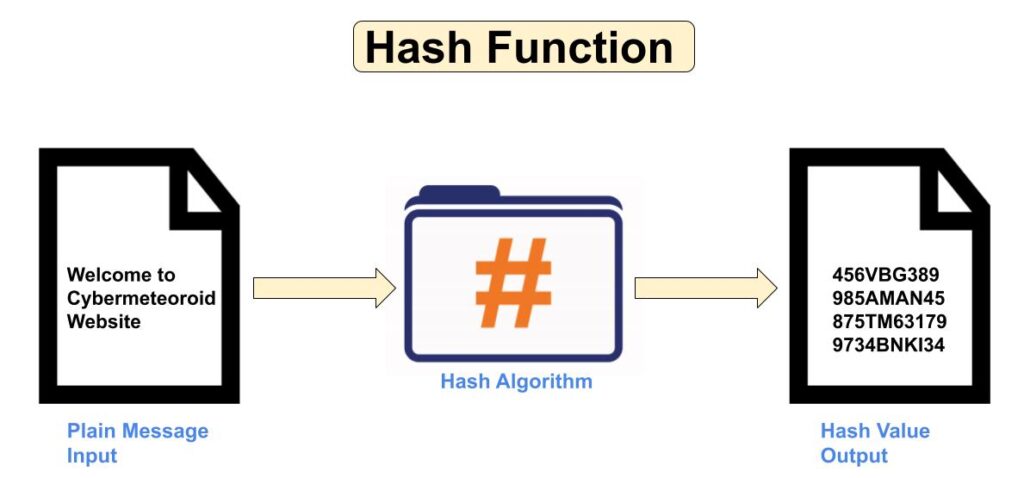
A Cryptographic Hash Function is a mathematical function that converts arbitrary input data into fixed-size output data. Values returned by this function are called hash values or message digest. It is easy to calculate and generate hash value but challenging to retrieve original data, means it is a one way function – input data is hashed into an algorithm that produces a fixed length unique string of data but is difficult to decrypt its original data. In hash function if any minor change is made in the input message, no matter how small change will result in a massive change in the output. This effect is known as Avalanche Effect in hash function. The main objectives of hash function are ensure data integrity, facilitating secure password storage, creating and verify digital signatures. Most widely used hash algorithms are
- Secure Hash Algorithm (SHA-1,2,3)
- Message Digest (MD5)
- LanMan Hash (LM Hash)
- NTLM (New Technology Lan Manager)
- RACE Integrity Primitives Evaluation Message Digest (RIPEMD)
- Whirlpool
How to Protect Keys in cryptography?
In Cryptography the only things that should be “secret” when it comes to a secure Communication are the keys themselves. Never store encryption/decryption keys in plain text along with the data that they protect. The most common methods for protecting keys are
- Always Store keys in a filesystem and protect them with strong access control lists (ACLs).
- Always encrypt your encryption keys with a second key encrypting key (KEK). The KEK should be generated using password-based encryption.
- Hardware Security Module (HSM) is an appliance for generating and storing cryptographic keys that is less susceptible to tampering than software based storage.
Related Contents
1. What is an IP address?
2. Difference between IPv4 & IPv6.
3. Difference between Public and Private IP Address.
4. What is DHCP Server?
5. What Is DORA Process in DHCP?
6. What is DNS Server and How Its work?
7. What is Ports and Protocols in computer networks?
8. How Proxy Server hides IP Addresses?
9. What is Firewall?
10. How DNS Server related to IP Address?
11. IDS Vs IPS in Security.
12. Difference between Hub, Switch & Router.

