International Data Encryption Algorithm (IDEA), also known as Improved Proposed Encryption Standard (IPES), is a symmetric-key block cipher encryption algorithm. IDEA encrypts a 64-bit block of plaintext to 64-bit block of cipher text. It uses a 128-bit key. For encryption, the 64-bit plain text is divided into four 16 bits sub-blocks. Each of these blocks goes through 8 rounds and a “half” round final transformation. In each of these eight rounds, some arithmetic and logical operations are performed to produce cipher text. IDEA encryption supports easy hardware & software implementation for quick execution. In real world IDEA encryption are used in audio and video for cable TV, voice over IP, email via public networks.
The main key points of International Data Encryption Algorithm (IDEA) are:
- 64-bit block of plaintext is given as input.
- This 64-bit plain text is divided into four 16 bits sub-blocks.
- The length of key is 128 bits.
- For encryption, total 8 rounds are performed.
Working of IDEA Encryption
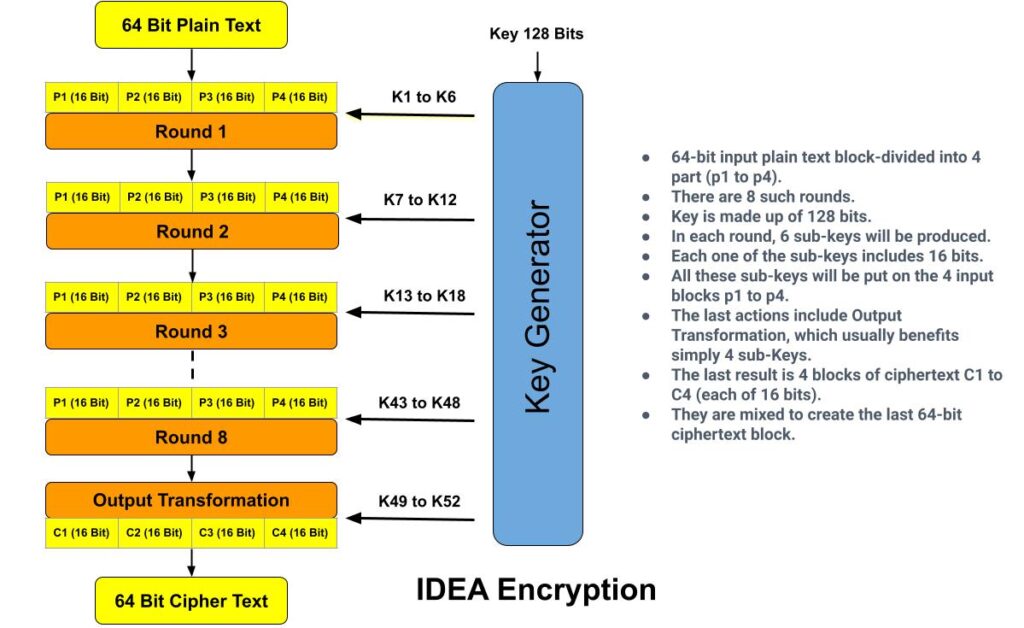
The process of encryption and decryption both are similar in IDEA encryption. It derives much of its security by interleaving operations from different groups –modular addition and multiplication, and bitwise exclusive OR (XOR).

By using a 128-bit key, IDEA encrypts a 64-bit block of plaintext into a 64-bit block of cipher-text. The plaintext block divided into four 16-bit sub blocks for each of the eight complete rounds, namely P1, P2, P3 and P4. Another process produces six 16-bit key sub blocks for each of the encryption rounds, namely K1, K2, K3, K4, K5 and K6.
In each complete round, three algebraic operations are performed: bitwise XOR, addition modulo 216 and multiplication modulo 216+1.
Encryption Steps of IDEA Algorithm
For one encryption round there are total 14 steps.
Step-1: Multiply P1 with K1.
Step-2: Add P2 and K2.
Step-3: Add P3 and K3.
Step-4: Multiply P4 and K4.
Step-5: Bitwise XOR the results of steps 1 and 3.
Step-6: Bitwise XOR the results of steps 2 and 4.
Step-7: Multiply the result of step 5 with K5.
Step-8: Add the results of steps 6 and 7.
Step-9: Multiply the result of step 8 with K6.
Step-10: Add the results of steps 7 and 9.
Step-11: Bitwise XOR the results of steps 1 and 9.
Step-12: Bitwise XOR the results of steps 3 and 9.
Step-13: Bitwise XOR the results of steps 2 and 10.
Step-14: Bitwise XOR the results of steps 4 and 10.
Six sub keys are used in each of the eight rounds and in final round (output transformation) only 4 keys are used. The steps involved are the following:
Step-1: Multiply P1 with K49.
Step-2: Add P2 and K50.
Step-3: Add P3 and K51.
Step-4: Multiply P4 and K52.
After the final round, we get as a result of Cipher Text of International Data Encryption Algorithm.
Decryption Process In IDEA Encryption
Decryption works like encryption, but the order of the round keys is inverted, and the subkeys for the odd rounds are inversed. For instance, the values of subkeys K1–K4 are replaced by the inverse of K49–K52 for the respective group operation, K5 and K6 of each group should be replaced by K47 and K48 for decryption.
Conclusion
IDEA is a well-known cipher that has been analyzed by many researchers for the past decade, and, yet, no attack against five or more of its 8.5 rounds has been found. The Simplified IDEA algorithm is not intended to be compared for efficiency or security with simplified versions of DES or AES. Due to its strength against cryptanalytic attacks and due to its inclusion in several popular cryptographic packages, IDEA is widely used.
Related Questions & Answers
1 What is cryptography?
Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information, so that only those for whom the information is intended can read and process it. In information Read more
2 What is DES Algorithm?
Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption designed by an IBM team and published by the National Institute of Standards and Technology (NIST).
It uses the same key to…Read more
3 What is Private Key Cryptography?
Symmetric cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message… Read more
4 Difference between DES & AES algorithm?
Data Encryption Standard (DES) and Advanced Encryption Standard (AES) algorithm, both are the symmetric block cipher. DES structure is based on feistal network while AES structure is based S-P network. Read more
5 What is Public Key Cryptography?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. he private key should not be… Read more
6 Difference between Stream & Block Cipher?
Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Both Stream Cipher and Block Cipher are…Read more

