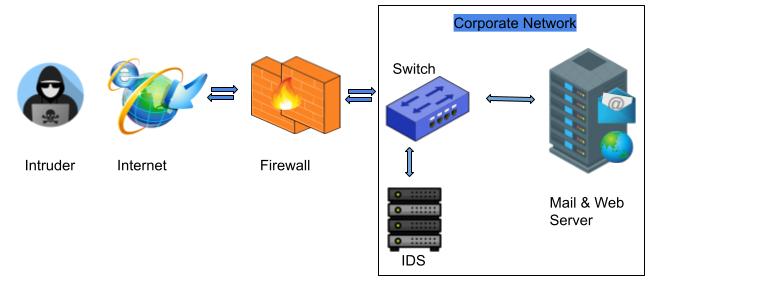
What Is IDS ?
An intrusion detection system (IDS) is a hardware appliance or software application that monitors traffic moving on networks and through systems to search for suspicious activity and known threats, when such activity is discovered it generates alerts. Based upon these alerts, a security operations center (SOC) analyst or incident responder can investigate and analyze the issue and take the appropriate actions to mitigate the threat.
IDS security technologies are ‘passive’ in nature rather than ‘active’ in nature. This means that they are designed to generate alerts on suspicious activity and does not take any action to prevent the organization network, and for this reason IDS deployed alongside intrusion prevention systems (IPS) which are ‘active’ in nature and take necessary action to prevent the internal network.
Corporates IT departments deploy intrusion detection systems to gain visibility into high potentially malicious activities happening within their internal environments Sometimes IDS generates false alarms. So, organization needs to fine tune or configure the IDS properly so that IDS recognized what is normal traffic on the private network looks like as compared to malicious activity.
Types of Intrusion Detection System (IDS)
Intrusion detection systems are designed to protect your organization internal network in different environments. Based on their deployment, IDS categories in two different types Network Based Intrusion detection system (NIDS) and Host Based Intrusion detection system (HIDS).
1. Network Based IDS
A network-based IDS solution is designed to monitor an entire secured internal network. NIDS is deployed at a calculated point or points within the network, where it can monitor inbound and outbound traffic to and from all the devices on the internal network. NIDS designed to help organizations monitor their cloud, on-premise and hybrid environments for suspicious or malicious activity that could indicate a compromise. Once an attack is identified or suspicious behavior is observed, the alert can be sent to the administrator (SOC Analyst) for further investigation and analyses. SOC analyst will take proper action on the alerts to mitigate the risk.
2. Host Based IDS
Host-based intrusion detection systems help organizations to monitor processes and applications running on endpoint devices such as servers and workstations and HIDS also monitors the incoming and outgoing packets from the endpoint devices. When any potentially malicious activity or event is found in host system HIDS immediately generates an alert. And sends an alert to the administrator to investigate it. Host-based intrusion detection systems are commonly deployed with network-based intrusion detection systems (NIDS) and SIEM solutions, which aggregate and analyse security events from multiple sources.
Detection Method of Intrusion Detection System (IDS)
1. Signature based Detection
Signature-based IDS solutions use fingerprints of known threats and malicious instruction sequences used by malware to identify them. Once malware or other malicious content has been identified, a signature is generated and added to the list used by the IDS solution to test incoming content. It also detect the threats on the basis of the specific patterns such as number of bytes or number of 1’s or number of 0’s in the network traffic. All alerts are generated based upon detection of known pattern or content so chances of false positive alerts are decreases. For signature based IDS, it is impossible to detect new attacks(zero day attack), or attack having no patterns.
2. Anomaly based Detection
Anomaly based IDS, newer solution designed to detect and adapt to unknown attacks. This detection method uses machine learning to create a trust worthy model. This trust worthy model established a baseline to determine what is considered normal for the network with respect to bandwidth, protocols, ports and other devices. If any new behavior is seen by IDS then it compares this new behavior with trust worthy model. If anything against the trustworthy model, it generates an alert and send the alert to the administrator to investigation. Anomaly based IDS is capable to detect new attacks (zero day attack), or attack having no patterns.
3. Hybrid Based Detection
Hybrid based IDS is combination of both IDS Signature based Detection IDS and Anomaly based Detection IDS. It uses both signature-based and anomaly-based detection to detect the threats which is known or unknown. This method reduce the false positive error rates. But the cost of hybrid based IDS solution is more as compared to signature & anomaly based.
IDS vs Firewall
IDS and firewall both are related to the network security device, but IDS monitors traffic moving on networks and through systems to search for suspicious activity and known threats, and it is passive in nature. On the other hand firewall is active in nature and monitor network packets and allows or blocks traffic based upon predefined rules. Basically firewall creates a boundary between your internal network and external network.


Hey there, You’ve performed an incredible job. I will certainly digg it and for my part recommend to my friends. I’m sure they will be benefited from this site.
great points altogether, you simply gained a brand new reader. What would you suggest about your post that you made a few days ago? Any positive?