What is Symmetric Key Cryptography ?
Symmetric key cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message. Symmetric key cryptography can be used on in-transit, at-rest and in-use data, but it is commonly only used on at-rest data, as sending the secret to the receiver of the message can lead to compromise. Confidentiality can be assured with symmetric encryption but key distribution can be challenging with it.
There are two types of symmetric encryption:
1. Block Cipher: A block cipher is an encryption technique that breaks down plaintext messages into fixed-size blocks then converts one block of the message at a time. Block cipher is used for database, file encryption. It is implement through a software solution.
2. Stream Cipher: A stream cipher, on the other hand, breaks down a plaintext message into single bits, then encrypts one byte of the message at a time. It uses mathematical XOR function to create cipher text. Encryption speed of stream cipher is faster as compared to block cipher. Stream cipher mostly used for SSL secure connection for web.
Most famous symmetric algorithms are
- Data Encryption Standard (DES)
- Triple DES (3DES)
- Advanced Encryption Standard (AES)
- International Data Encryption Algorithm (IDEA)
- Blowfish and Twofish
- Rivest Cipher (RC)
Data Encryption Standard (DES)
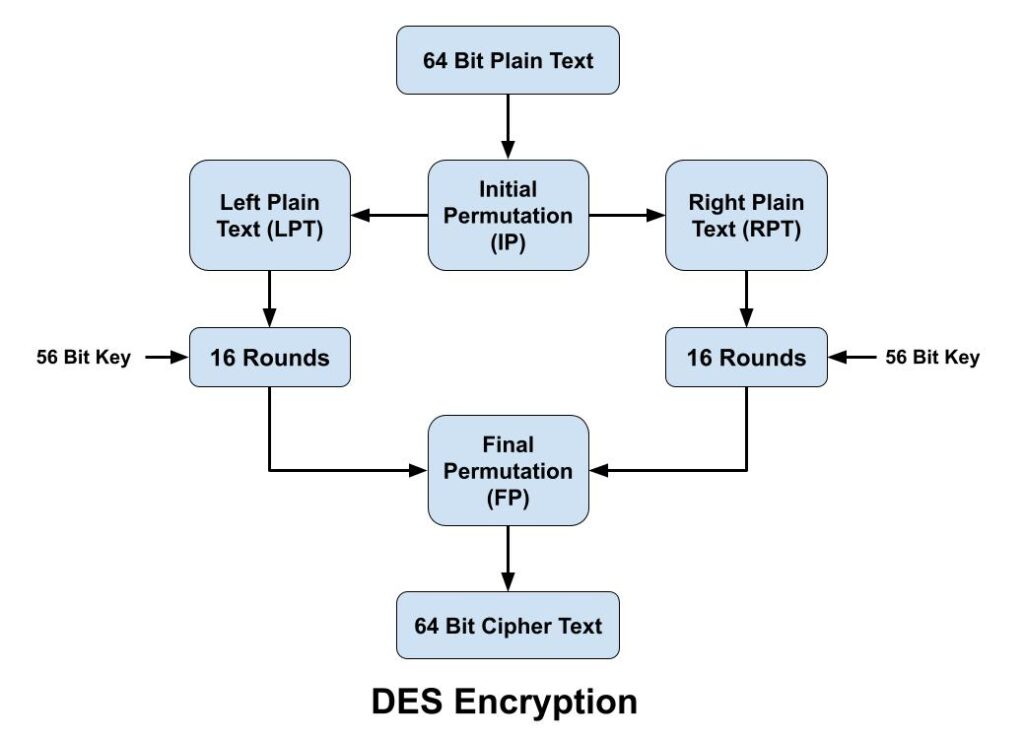
The Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption designed by an IBM team and published by the National Institute of Standards and Technology (NIST). It is symmetric key cryptography, so it uses the same key to encrypt and decrypt a message and key length is 56 bits. DES is a block cipher and encrypts data in blocks size of 64 bits each, which means 64 bits of plaintext goes as the input to DES, and produces 64 bits of cipher text.
The DES algorithm encryption process breaks down into the following steps:
- In first step, the 64-bit plain text block is handed over to an initial Permutation (IP) function.
- Initial permutation (IP) is then performed on the given plain text.
- The IP produces two halves of the permuted block, known as Left Plain Text (LPT) and Right Plain Text (RPT).
- Both LPT and RPT go through 16 rounds of the encryption process.
- Finally, both LPT and RPT are recombined, and a Final Permutation (FP) is performed on the newly combined block.
- Finally 64-bit cipher text is produced.
Triple DES (3DES)
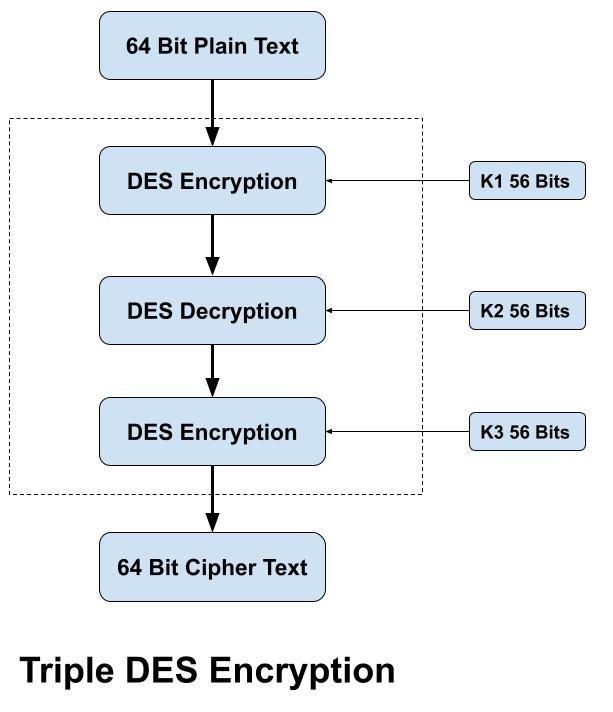
The Triple Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption. It uses the Data Encryption Standard (DES) cipher three times to encrypt its data that why it is referred as 3DES. It operates in three basic steps: Encrypt-Decrypt-Encrypt (EDE). It works by taking three 56-bit keys (K1, K2 and K3), encrypting with the first key (k1), decrypting with the second key (k2), and encrypting with the third key (k3). A two-key variant also exists, where k1 and k3 are the same. Note that if K1 = K2 = K3, then Triple DES is really Single DES.
The 3DES algorithm process breaks down into the following steps:
- Encrypt the plaintext using the DES algorithm with first key (K1).
- Decrypt the resulting encrypted output using the DES algorithm with second key (K2).
- Encrypt the resulting decrypted output using the DES algorithm with third key (K3).
Although 3DES is more secure than DES, but it still remains vulnerable to certain kinds of attacks like meet-in-the middle attack and block collision attack.
Advanced Encryption Standard (AES)
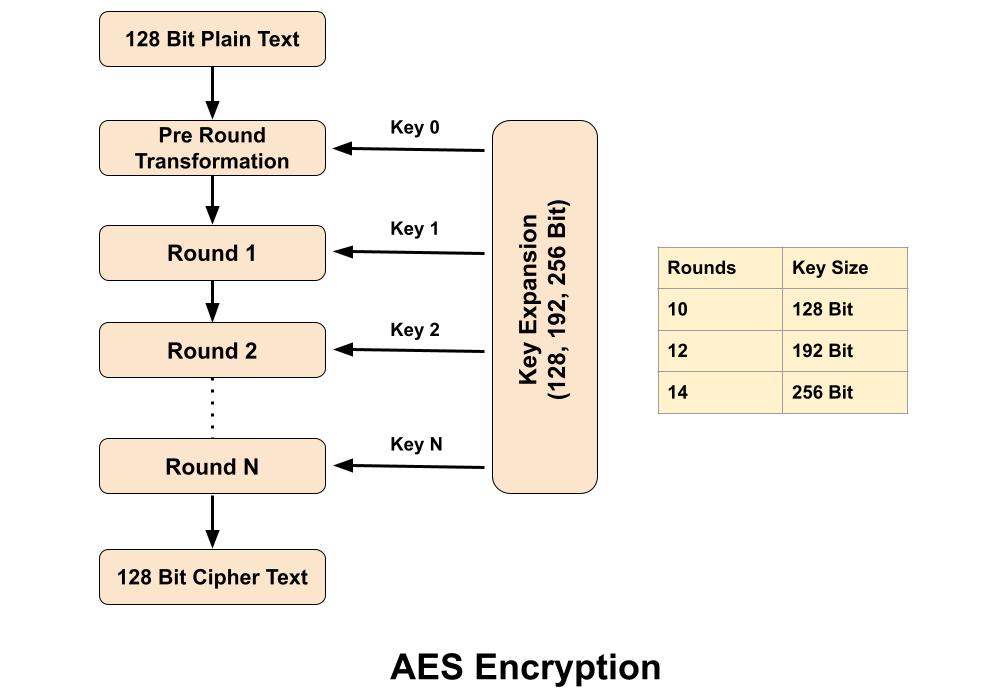
The Advanced Encryption Standard (AES) algorithm is a symmetric-key block cipher (block size 128 bit) encryption designed & by published by the National Institute of Standards and Technology (NIST) in 2001. AES is widely used today as it is a much stronger than DES and 3DES. In Advanced Encryption Standard number of rounds depends on the key length, 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys.
Advanced Encryption Standard takes 128 bits plain text as input and produced 128 bits cipher text as output. It’s encryption process is based on a substitution-permutation network, also referred as an SP network. It consists of a series of linked operations, including replacing inputs with specific outputs (substitutions) and others involving bit shuffling (permutations).
International Data Encryption Algorithm (IDEA)
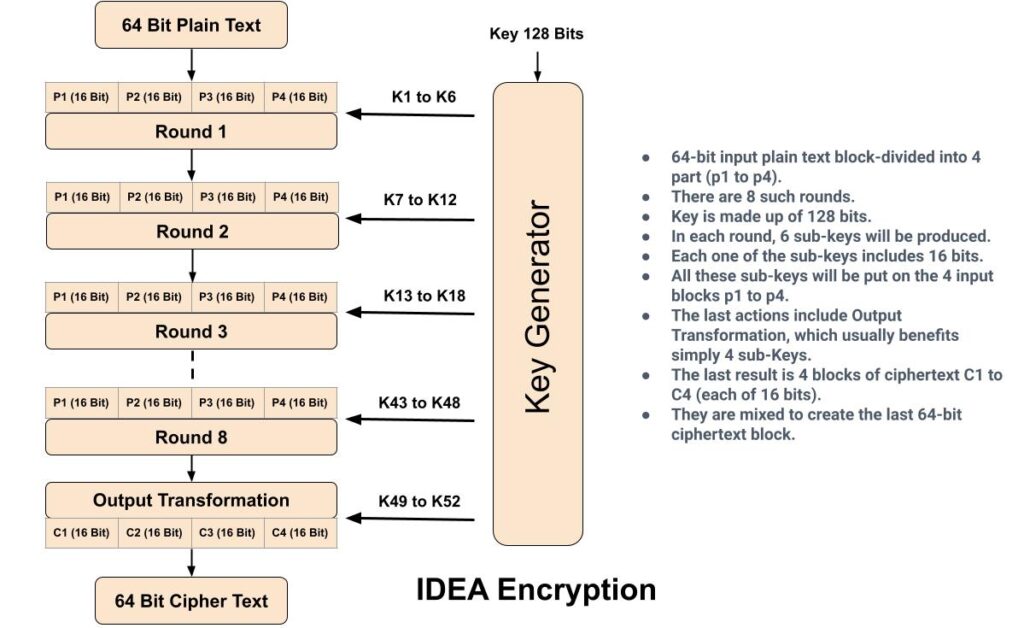
International Data Encryption Algorithm (IDEA), also known as Improved Proposed Encryption Standard (IPES), is a symmetric-key block cipher encryption algorithm. IDEA encrypts a 64-bit block of plaintext to 64-bit block of cipher text. It uses a 128-bit key. For encryption, the 64-bit plain text is divided into four 16 bits sub-blocks. Each of these blocks goes through 8 rounds and a “half” round final transformation. In each of these eight rounds, some arithmetic and logical operations are performed to produce cipher text. IDEA encryption supports easy hardware & software implementation for quick execution. In real world IDEA encryption are used in audio and video for cable TV, voice over IP, email via public networks.
Blowfish and Twofish
Blowfish is an encryption technique introduced in 1993 by Bruce Schneier. Blowfish is a symmetric block cipher that can be used as a replacement for DES or IDEA. Blowfish has a 64-bit block size and a variable key length from 32 bits up to 448 bits. It is a 16-round Feistel cipher. It is significantly faster than DES and provides a good encryption rate. Blowfish is unpatented and license-free, and is available free for all uses.
Twofish is the successor to Blowfish, it is a symmetric-key block cipher with a block size of 128 bits and variable-length key of size 128, 192 or 256 bits. This technique is one of the fastest encryption algorithms and is ideal for both hardware and software environments. It was a selected for the National Institute of Technology and Science (NIST) to find a replacement for the Data Encryption Standard (DES) encryption algorithm but in the end it was not selected for standardization. It is completely free, and there are no patent royalties on the algorithm, copyright on the code, or any license fees.
Rivest Cipher
The Rivest Cipher (RC) algorithms are a set of symmetric-key cryptography algorithms created by Ron Rivest. There are total 6 types of Rivest Cipher (RC) algorithms.
RC1: The main idea of RC1 algorithm was to design a Symmetric Key cryptography algorithm that could be used by the users to protect their data as it passes through the network. But it was never published. Because different variants were designed and continuous research has been carried out by the researchers.
RC2: was a 64-bit block cipher introduced in 1987. It was considered as a proposal for the DES replacement. The input and output block size of this algorithm was 64-bit each with variable key size from 1 byte to 128 bytes.
RC3: was broken before ever being used. RC3 was broken before ever being used. When the RC3 algorithm was being developed at RSA security, It was broken at the same time. Hence, it was not used.
RC4: is a stream cipher, symmetric key encryption algorithm. It encrypts messages one byte at a time via an algorithm. RC4 is the most popular among all RC algorithms. It’s simple to apply, and it works quickly, even on very large pieces of data. For encryption it uses variable key size from 40 bits to 2048 bits. RC4 encryption algorithm is used by standards such as IEEE 802.11 within WEP and application like TLS/SSL also used RC4 encryption.
RC5: RC5 is a block cipher algorithm based on the symmetric key, designed by Ronald Rivest for RSA Data in 1994. In RC5 the size of plain text block can be of 32 bits, 64 bits or 138 bits and length of the key can be of 0 to 2040 bits. The output generated by RC5 is the cipher text which has the size the same as plain text size. The main features of RC5 are, it is quite fast as it uses only primitive computer operations and it requires less memory for execution.
RC6: It is a block cipher which uses 128 bit block size and supports key sizes of 128, 192 and 256 bits. RC6 was developed for an advanced encryption standard (AES) competition but was not selected by NIST. It is an improvement of the RC5 Algorithm. It provides even better security against attacks which may be possible in the RC5 Algorithm. It uses 4 register which make it faster than its previous version.
Related Content
1. What is an IP address?
2. Difference between IPv4 & IPv6.
3. Difference between Public and Private IP Address.
4. What is DHCP Server?
5. What Is DORA Process in DHCP?
6. What is DNS Server and How Its work?
7. What is Ports and Protocols in computer networks?
8. How Proxy Server hides IP Addresses?
9. What is Firewall?
10. How DNS Server related to IP Address?
11. IDS Vs IPS in Security.
12. Difference between Hub, Switch & Router.