Threat Hunting
Threat Hunting is a cyber security technique designed to detect presence of threat that have not been discovered by a normal security monitoring. It consists of searching iteratively through networks to detect indicators of compromise (IoCs), hacker tactics, techniques, and procedures (TTPs), and threats such as Advanced Persistent Threats (APTs) evading your existing security system. Threat Hunting is potentially less disruptive that penetration testing.
Threat hunting activities include:
- Hunting for internal threats or external attackers: cyber threat hunters can detect threats posed by insiders, an organization member of the staff, or an intruder, like a criminal organization.
- Seeking for hidden threats to prevent the attack from happening: by continuously monitoring, threat hunters analyze the organization computing environment. They use behavioral analysis to detect anomalies indicating a threat to an organization.
- Proactively hunting for known adversaries: a known attacker is one who is listed in threat intelligence services, or whose code pattern matches the blacklist of known malicious programs.
- Executing the incident response plan: when a threat hunters detect a threat, they gather as much information as possible before executing the incident response plan to neutralize it. This is used to update the response plan and prevent similar attacks.
Threat Hunting Loop
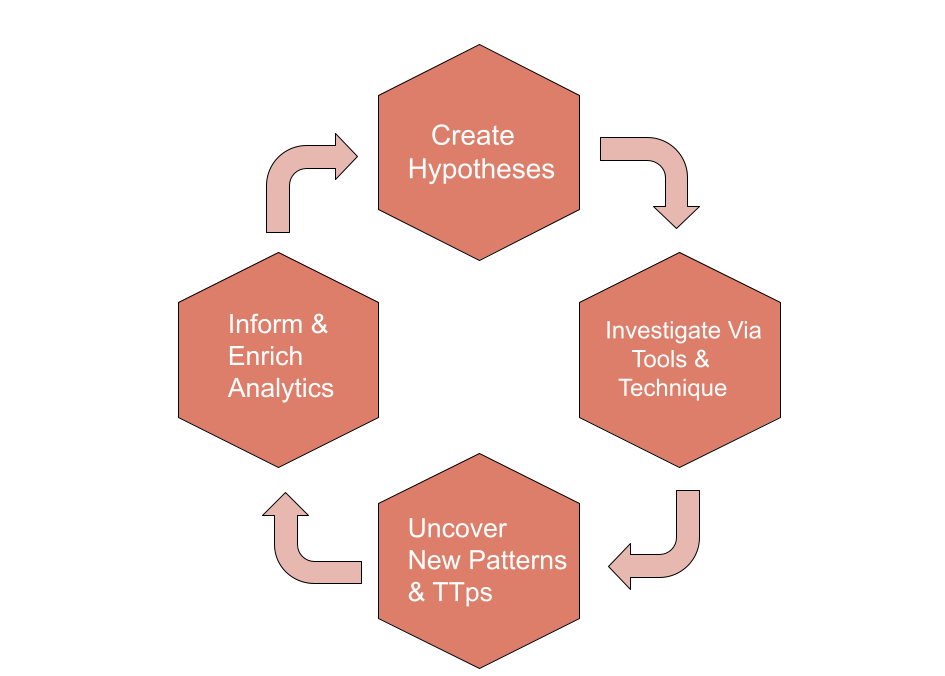
Hypothesis Generation
A hunt starts with creating a hypothesis, or an educated guess, about some type of activity that might be going on in your IT environment. An example of a hypothesis could be that users who have recently traveled abroad are at elevated risk of being targeted by state-sponsored threat actors, so you might begin your hunt by planning to look for signs of compromise on their laptops or assuming that their accounts are being misused around your network. Each of these subhypotheses would be tested individually. Analysts can develop hypotheses manually based on this type of intelligence.
Tool and Technique Enabled Investigation
Second, hypotheses are investigated via various tools and techniques, including Linked Data Analysis and visualizations. Effective tools will leverage both raw and linked data analysis techniques such as visualizations, statistical analysis, or machine learning to fuse disparate cybersecurity datasets. Linked Data Analysis is particularly effective at laying out the data necessary to address the hypotheses in an understandable way, and so is a critical component for a hunting platform. Linked data can even add weights and directionality to visualizations, making it easier to search large data sets and use more powerful analytics.
Many other complementary techniques exist, including row-oriented techniques like stack counting and datapoint clustering. Analysts can use these various techniques to easily discover new malicious patterns in their data and reconstruct complex attack paths to reveal an attacker’s Tactics,Techniques, and Procedures (TTPs).
Pattern and TTP Discovery
Next, tools and techniques uncover new malicious patterns of behavior and adversary TTPs. This is a critical part of the hunting cycle. Let assume after investigation revealed that a user account has been behaving anomalously, with the account sending an unusually high amount of outbound traffic. After conducting a Linked Data investigation, it is discovered that the user’s account was initially compromised via an exploit targeting a third party service provider of the organization. This TTP (initial compromise via a third party system via particular type of malware)should be recorded, shared (both internally and externally), and tracked within the context of a larger attack campaign. Linked data relationships will also contextually reveal what other accounts were associated with the compromised third party service.
Automated Analytics
Lastly, successful hunts form the basis for informing and enriching automated analytics. Don’t waste your team’s time doing the same hunts over and over. Once you find a technique that works to find threats, automate it via an analytic so that your team can continue to focus on the next new hunt. There are many ways this can be done, including developing a saved search to run regularly, creating new analytics using tools like Sqrrl, Apache Spark, R, or Python, or by even providing feedback to a supervised machine learning algorithm confirming that an identified pattern is malicious.
Hunting Models
- Intel-based hunting: Intel-based hunts use IoCs, hash values, IP addresses, domain names and networks or host artifacts provided by intelligence sharing platforms such as computer emergency response teams (CERTs). An automated alert can be exported from these platforms and input into the SIEM as Structured Threat Information eXpression (STIX) and Trusted Automated Exchange of Intelligence Information (TAXII). Once the SIEM has the alert based on an IoC, the threat hunter can investigate the activity before and after the alert to identify any compromise in the environment.
- Hypothesis hunting: Hypothesis-based hunts use the IoAs and TTPs of attackers. The hunter identifies the threat actors based on the environment, domain and attack behaviors employed to create a hypothesis in alignment with the MITRE framework. Once a behavior is identified, the threat hunter monitors activities for any patterns in order to detect, identify and isolate the threat.
- Custom hunting: This model is based on situational awareness and industry-based hunting methods. It identifies anomalies in the SIEM and EDR tools and is customizable based on customer requirements. Custom or situational hunts are based on requirements received from customers or proactively executed based on situations, such as geopolitical issues and targeted attacks. These hunting activities can draw on both intel- and hypothesis-based hunting models using IoA and IoC information.
Read More
What is cybersecurity & why it is important ?
CIA Triad & AAA in Information Security
What is malware and its different types ?


I am new in threat hunting,Can you guide me which tool is good for beginner