The Rivest Cipher (RC) algorithms are a set of symmetric-key cryptography algorithms created by Ron Rivest. There are total 6 types of Rivest Cipher (RC) algorithms but Rivest Cipher RC4 algorithm is the most popular and widely used encryption among all 6 RC encryption.
RC4: is a stream cipher, symmetric key encryption algorithm. It encrypts messages one byte at a time via an algorithm. RC4 is the most popular among all RC algorithms. It’s simple to apply, and it works quickly, even on very large pieces of data. RC4 algorithm is used by standards such as IEEE 802.11 within WEP and application like TLS/SSL also used RC4 encryption.
Working of RC4 Algorithm
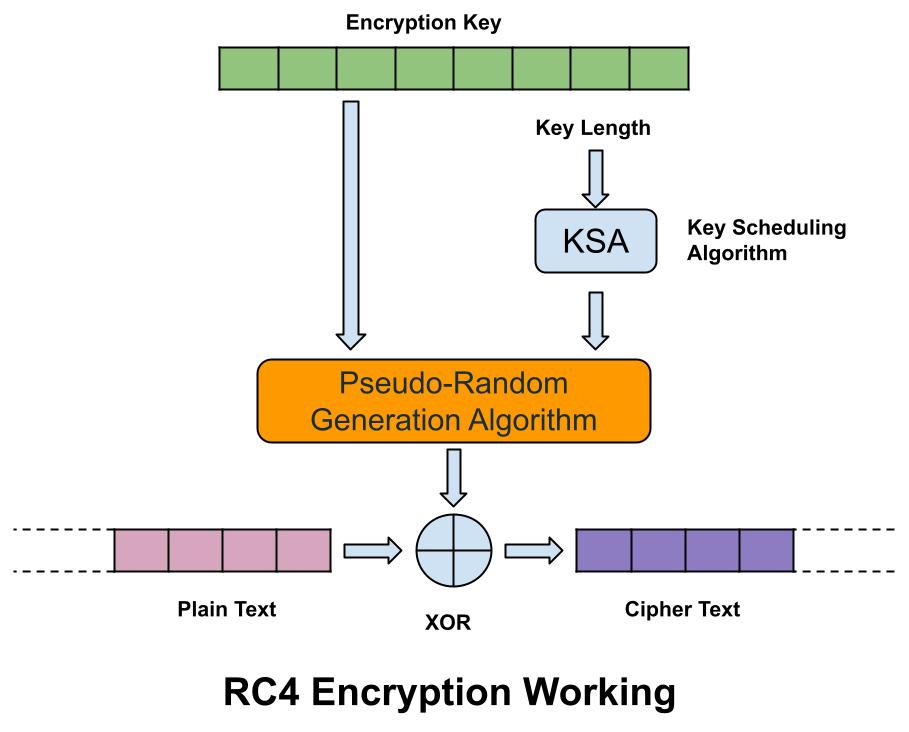
RC4 algorithm is a variable key-size stream cipher using either 64-bit or 128-bit sizes. The cipher uses a permutation and two 8-bit index-pointers to generate the keystream. The permutation itself is done with the Key Scheduling Algorithm (KSA) that then is entered into a Pseudo-Random Generation Algorithm (PRG), which generates a bitstream. Bit stream that the RC4 generates is as long as the plaintext stream. Then through the Exclusive OR (X-OR) operation, the bitstream and the plaintext generate the ciphertext.
When we put a plaintext and an encryption key in RC4 algorithm engine, then it generates keystream bytes with the help of the both Key Scheduling Algorithm (KSA) and the Pseudo-Random Generation Algorithm. The X-OR operation is executed byte-by-byte, and the byte output is the encrypted text.
Variants of RC4 Algorithm
- Spritz – Spritz is used to create cryptographic hash functions and deterministic random bit generator.
- RC4A – This is a variant that was proposed to be faster and stronger than the average RC4 cipher. But there were issues with randomization of numbers in the cipher.
- VMPC – Variably Modified Permutation Composition (VMPC) is a version of RC4. But also struggling with number randomization.
- RC4A+ — a more detailed, longer and advanced version of RC4, and RC4A with a three-phase key schedule, and has proven to be more secure.
Other Types of Rivest Cipher
Rivest Cipher 1 (RC1)
The main idea of RC1 algorithm was to design a Symmetric Key cryptography algorithm that could be used by the users to protect their data as it passes through the network. But it was never published. Because different variants were designed and continuous research has been carried out by the researchers.
Rivest Cipher 2 (RC2)
RC2 was a 64-bit block cipher introduced in 1987. It was considered as a proposal for the DES replacement. The input and output block size of this algorithm was 64-bit each with variable key size from 1 byte to 128 bytes.
Rivest Cipher 3 (RC3)
RC3 was broken before ever being used. RC3 was broken before ever being used. When the RC3 algorithm was being developed at RSA security, it was broken at the same time. Hence, it was not used.
Rivest Cipher 5 (RC5)
RC5 is a block cipher algorithm based on the symmetric key, designed by Ronald Rivest for RSA Data in 1994. In RC5 the size of plain text block can be of 32 bits, 64 bits or 138 bits and length of the key can be of 0 to 2040 bits. The output generated by RC5 is the cipher text which has the size the same as plain text size. The main features of RC5 are, it is quite fast as it uses only primitive computer operations and it requires less memory for execution.
Rivest Cipher 6 (RC6)
It is a block cipher which uses 128 bit block size and supports key sizes of 128, 192 and 256 bits. RC6 was developed for an advanced encryption standard (AES) competition but was not selected by NIST. RC6 is an improvement of the RC5 Algorithm. It provides even better security against attacks which may be possible in the RC5 Algorithm. It uses 4 register which make it faster than its previous version.
Comparison between RC Algorithms
| Algorithms | RC2 | RC4 | RC5 | RC6 |
| Year | 1987 | 1987 | 1994 | 1998 |
| Cipher | Block | Stream | Block | Block |
| Block size | 64 bits | 2064 bits | 32, 64,128 bits | 128, 256 bits |
| Key size | 8-128 bits | 1-256 bits | 0-2048 bits | 128,192,256 bits |
| Rounds | 16 rounds | 256 rounds | 0-255 rounds | 20 recommended |
| Possible Attacks | Differential, Linear | Beast | Differential | Correlation |
Related Questions & Answers
1 What is cryptography?
Cryptography is the practice and study of writing & solving codes in order to hide the true meaning of information, so that only those for whom the information is intended can read and process it. In information Read more
2 What is DES Algorithm?
Data Encryption Standard (DES) algorithm is a symmetric-key block cipher encryption designed by an IBM team and published by the National Institute of Standards and Technology (NIST).
It uses the same key to…Read more
3 What is IDEA Algorithm?
International Data Encryption Algorithm (IDEA), also known as Improved Proposed Encryption Standard (IPES), is a symmetric-key block cipher encryption algorithm. Read more
4 What is AES Algorithm?
AES encryption process is based on a substitution-permutation network. AES encryption treats the 128 bits of a plaintext block as 16 bytes. Read more
5 What is Private Key Cryptography?
Symmetric cryptography also popular as private key cryptography, uses a single key to encrypt data. In this algorithm both sender and receiver share a same secret key for encrypting and decrypting the message… Read more
6 Difference between DES & AES algorithm?
Data Encryption Standard (DES) and Advanced Encryption Standard (AES) algorithm, both are the symmetric block cipher. DES structure is based on feistal network while AES structure is based S-P network. Read more
7 What is Public Key Cryptography?
Asymmetric Cryptography also popular as public key cryptography, uses two keys to encrypt data. One key is used for data encryption, while the other key is used for data decryption. he private key should not be… Read more
8 Difference between Stream & Block Cipher?
Both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Read more

