What Is IPS ?
An intrusion prevention system (IPS) is an automated network security device (which can be a hardware or software) is used to identify malicious activity, record detected threats, report detected threats and take preventative action to stop a threat from doing damage. An IPS tool can be used to continually monitor network traffic in real time.
Intrusion prevention system (IPS) is more advance as compared to an intrusion detection system (IDS), which simply detects malicious or suspicious activity but cannot take action against it just generate an alarm and inform to administrator. While Intrusion prevention systems are able to detect malicious or suspicious activity and take necessary action to stop it. IPS is part of a unified threat management (UTM) or next-generation firewall (NGFW) solution. IPS is powerful enough to scan a high volume of network traffic without slowing down network performance.
Types of IPS
Four types of intrusion prevention systems are commonly used. These types are the following:
1. Network-based Intrusion Prevention System (NIPS)
A network-based intrusion prevention system (NIPS) solution is designed to monitor an entire internal private network. NIPS is installed only at strategic points or points within the network, where it can monitor inbound and outbound traffic to and from all the devices on the internal network. If anything suspicious found in traffic. NIPS takes necessary action to prevent from it.
2. Host-based Intrusion Prevention System (HIPS)
Host-based intrusion prevention system (HIPS) is installed on an endpoint devices (such as workstation & Server) and to monitor processes and applications running on endpoint devices and HIPS also monitors the incoming and outgoing packets from the endpoint devices. If any malware or suspicious activity found in endpoint or host devices. HIPS takes necessary action to prevent from it.
3. Network behavior analysis (NBA)
Network behavior analysis (NBA) examines network traffic to identify threats or malicious activity that generates strange traffic flows. The most common threats being distributed denial of service (DDoS) attacks and policy violation. If any suspicious traffic is detected in network. Network behavior analysis (NBA) immediately takes necessary action to prevent your network.
4. Wireless Intrusion Prevention System (WIPS)
This type of IPS simply scans a wireless network for unauthorized access and kicks unauthorized devices off the network. Basically WIPS monitors a wireless network for suspicious traffic by analyzing wireless networking protocols such as Wi-fi, Bluetooth/Bluetooth Low Energy (BLE), LORA-WAN, Sigfox, Near-Field Communication (NFC), 4G/5G, Zigbee etc.
Detection Method of Intrusion Prevention System (IPS)
Signature-Based Detection
Signature-based IPS solutions use fingerprints of known threats and malicious instruction sequences used by malware to identify them. IPS also detect the threats on the basis of the specific patterns such as number of bytes or number of 1’s or number of 0’s in the network traffic. Once a known threat is identified by IPS in network, it generates an alert and takes all preventive steps to avoid damage. Also IPS sends the alert info to the administrator to investigation. Signature based IPS is not capable to detect new attacks (zero day attack), or attack having no patterns.
Statistical Anomaly-Based Detection
Statistical anomaly-based detection method uses machine learning to create a trust worthy model. This trust worthy model established a baseline to determine what is considered normal for the network with respect to bandwidth, protocols, ports and other devices. If any new behavior is seen by IPS then it compares this new behavior with the standard baseline. If anything found against the baseline performance, it generates an alert and takes all preventive actions to avoid damage. This method is more advanced intrusion prevention systems use artificial intelligence (AI) and machine learning technology to support anomaly-based monitoring. But still chances of triggering of false positive alerts are high. Statistical anomaly based IPS is capable to detect new attacks (zero day attack), or attack having no patterns.
Policy-Based Detection
In policy based detection method, an administrator is required to make security policies in IPS — when an event occurs that breaks a defined security policy, an alert is generated and sent to system administrator.
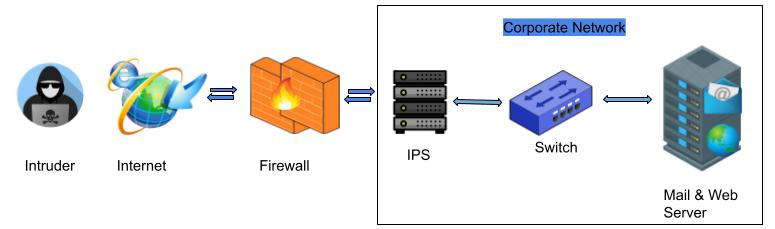
IPS VS Firewall
Intrusion Prevention System (IPS) and firewall both are related to the network security device, but IPS is used to identify malicious activity, record detected threats, report detected threats and take preventative action to stop a threat from doing damage. On the other hand firewall monitors network packets and allows or blocks traffic based upon predefined rules. Basically firewall creates a boundary between your internal network and external network. Over the internet there is hackers and malware traffic tried to penetrate into internal network. Firewall blocks these unwanted harmful traffic and keep safe internal network.
Benefits of Intrusion Prevention System (IPS)
- Intrusion Prevention System (IPS) is Active in nature means after detecting the threat it takes preventive actions.
- Intrusion Prevention System (IPS) is capable of mitigating attacks such as zero-day threats, DoS/DDoS attacks and brute-force attack attempts.
- Automatically notifying administrators when suspicious traffic is found. And allow or deny specific incoming traffic to a network.
- Anomaly based IPS solutions are capable to detect new attacks (zero day attack), or attack having no patterns.
- Intrusion Prevention System (IPS) can be set up with customized security policies and rules to provide security controls specific to the organizations that uses it.
Disadvantages of Intrusion Prevention System (IPS)
- When IPS blocks abnormal activity on a network assuming it is malicious but it may be false positive.
- Intrusion Prevention System (IPS) is very expensive as compared to Intrusion Detection System (IDS).
- Signature-based Intrusion Prevention System needs proper updates to recognize the latest threats.


4 thoughts on “Intrusion Prevention System (IPS) In Network Security.”