Stream Cipher and Block Cipher, both are the techniques used for encryption and decryption of data, i.e. to convert the plaintext to cipher text and cipher text to plaintext. Both Stream Cipher and Block Cipher are used for the same purpose, but there is a difference in their working. Block Cipher and Stream Cipher belong to the symmetric key cipher. Stream cipher breaks down a plaintext message into single bits then encrypts one byte of the message at a time. It uses mathematical XOR function to create cipher text. While Block cipher breaks down plaintext messages into fixed-size blocks then converts one block of the message at a time. . Stream cipher mostly used for SSL secure connection for web and Block cipher is used for database, file encryption.
Major differences between Stream Cipher and Block Cipher are given below table.
| Key Parameters | Stream Cipher | Block Cipher |
| Definition | A stream cipher, on the other hand, breaks down a plaintext message into single bits, then encrypts one byte of the message at a time. | A block cipher is an encryption technique that breaks down plaintext messages into fixed-size blocks then converts one block of the message at a time. |
| Conversion of Bits | Stream cipher uses 8 bits. | In other hand, Block cipher uses either 64 bits or more than 64 bits. |
| Speed | Stream cipher is fast in comparison to block cipher. | Block cipher is slow as compared to a stream cipher. |
| Techniques Used | Stream Cipher uses substitution techniques. | While Block Cipher uses transposition techniques. |
| Key Used | One key is used only one time in stream cipher. | One key is used multiple times in block cipher. |
| Confusion and Diffusion | It Relies only confusion. | It Uses both confusion and diffusion. |
| Implementation | The main implementation of Stream Cipher is Vernam Cipher. | While on the other side, The main implementation of Block Cipher is Feistel Cipher. |
| Reversibility | Due to use of XOR for the encryption, reverse encrypted text is easy. | In block cipher, reverse encrypted text is hard. |
| Algorithm Modes | Stream cipher uses CFB (Cipher Feedback) and OFB (Output Feedback) algorithm mode. | Block cipher uses ECB (Electronic Code Book) and CBC (Cipher Block Chaining) algorithm mode. |
| Example | OTP (One Time Pad) and Rivest Cipher 4 (RC4) | DES, 3DES and AES |
What Is Block Cipher ?
A block cipher is an encryption technique that breaks down plaintext messages into fixed-size blocks then converts one block of the message at a time. Block cipher is used for database, file encryption. It is implement through a software solution. For example, let’s say you have the message: “DC is better than marvel ”.
For encrypting this message using block cipher, the message would be broken down into smaller blocks of binary. So, “DC is better than marvel” would look something like this:
01000100010000110010000001101001011100110010000001100010011001010111010001110100 01100101011100100010000001110100011010000110000101101110001000000110110101100001 0111001001110110011001010110110000100000
If we break these 200 binary digits into blocks of, say, 4 digits, it divides nicely because 4 goes into 200 a total of 50 times. The blocks would look something like this:

Suppose if there isn’t enough data to form a complete block, Like say, if you had 202 binary digits instead of 200 then we simply add padding (set of 0s) in the end of the block.
The simplified version of a block cipher illustrates below how block ciphers work overall. Block cipher modes of operation have been developed to eliminate the chance of encrypting identical blocks of text the same way, the cipher text formed from the previous encrypted block is applied to the next block. A block of bits called an initialization vector (IV) is also used by modes of operation to ensure cipher texts remain different even when the same plaintext message is encrypted a number of times.
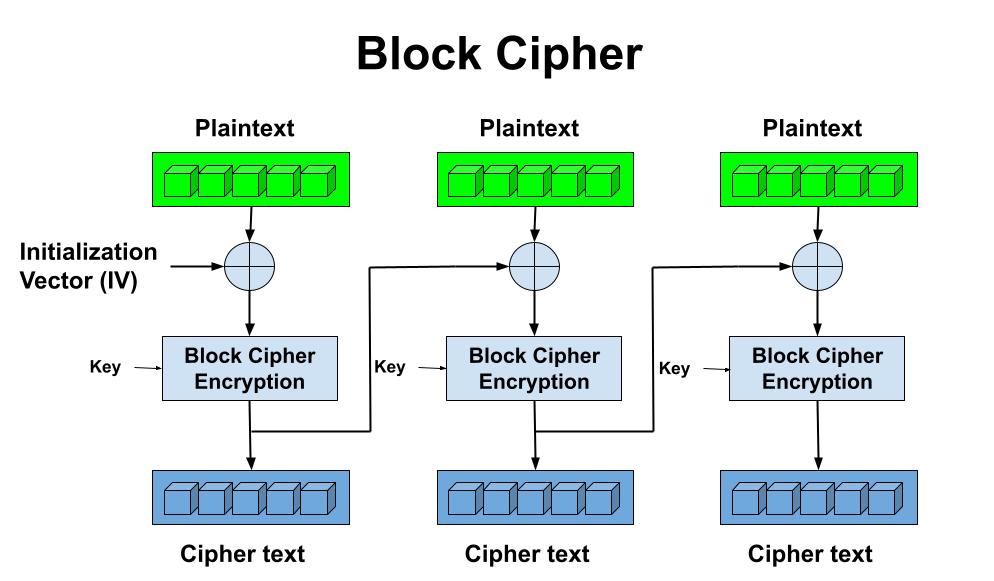
Where an IV is crossed with the initial plaintext block and the encryption algorithm is completed with a given key and the cipher text is then outputted. This resultant cipher text is then used in place of the IV in subsequent plaintext blocks.
Most famous modes of operation for block ciphers are CBC (cipher block chaining), CFB (cipher feedback), CTR (counter) and GCM (Galois/Counter Mode).
Advantages and Disadvantages of Block Cipher
- High diffusion: information from one plaintext symbol is diffused into several cipher text symbols.
- Immunity to tampering: difficult to insert symbols without detection.
- Slowness of encryption: an entire block must be accumulated before encryption / decryption can begin.
- Error Propagation: An error in one symbol may corrupt the entire block.
What Is Stream Cipher ?
A stream cipher, on the other hand, breaks down a plaintext message into single bits, then encrypts one byte of the message at a time. It uses mathematical XOR function to create cipher text. Encryption speed of stream cipher is faster as compared to block cipher. Stream ciphers are linear, so the same key is used for both encrypts and decrypts the messages. Stream cipher mostly used for SSL secure connection for web.
To better understand this, let’s take an example. A plaintext message “I am Batman”, the binary version of this plaintext message would look like this:
01001001001000000110000101101101001000000100001001100001011101000110110101100001 01101110
We know that stream cipher to encrypt the message bit by bit or one bit at a time. So, the plaintext data would be broken down into individual bits, which would look something like this:

The simplified version of a stream cipher illustrates below how stream ciphers work overall.
For Encryption: Plain Text and Keystream (A set of random characters replaces those in the plaintext. They could be numbers, letters, or symbols) produces Cipher Text .Same keystream will be used for decryption. The Plaintext will undergo XOR operation with keystream bit-by-bit and produces the Cipher Text.
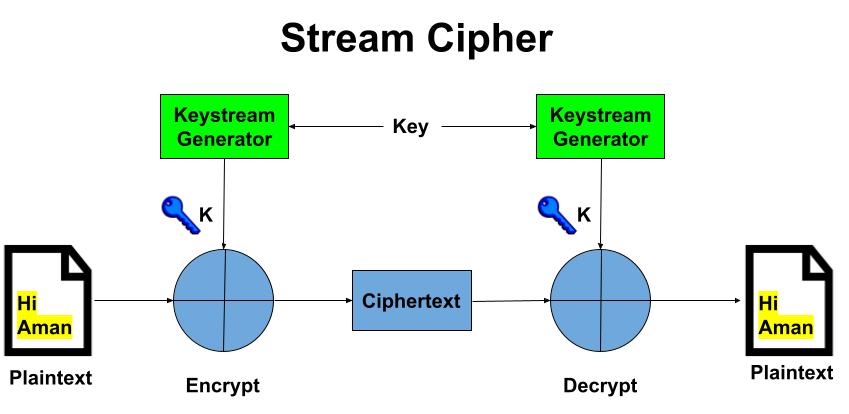
For Decryption: Cipher Text and Keystream gives the original Plain Text .Same keystream will be used for encryption. The Ciphertext will undergo XOR operation with keystream bit-by-bit and produces the actual Plain Text. Decryption is just the reverse process of Encryption i.e. performing XOR with Cipher Text.
Advantages and Disadvantages of Stream Cipher
- Stream algorithms are faster and more efficient than block ciphers because they’re encrypting only one bit of data at a time.
- It’s easy to incorporate stream ciphers into modern programs, and developers don’t need complex hardware to make it happen.
- Stream ciphers are vulnerable to many attacks like bit-flipping attacks and key reuse attacks.
Learn More About Cryptography
- What is Cryptography?
- What is Symmetric Key Algorithm?
- What is Public Key Cryptography?
- What is Digital Signature?
- What is Data Encryption Standard (DES)?
- What is Advanced Encryption Standard (AES)?
Related Content
1. What is an IP address?
2. Difference between IPv4 & IPv6.
3. Difference between Public and Private IP Address.
4. What is DHCP Server?
5. What Is DORA Process in DHCP?
6. What is DNS Server and How Its work?
7. What is Ports and Protocols in computer networks?
8. How Proxy Server hides IP Addresses?
9. What is Firewall?
10. How DNS Server related to IP Address?
11. IDS Vs IPS in Security.
12. Difference between Hub, Switch & Router.

Thanks for explaining block cipher working in simple words.